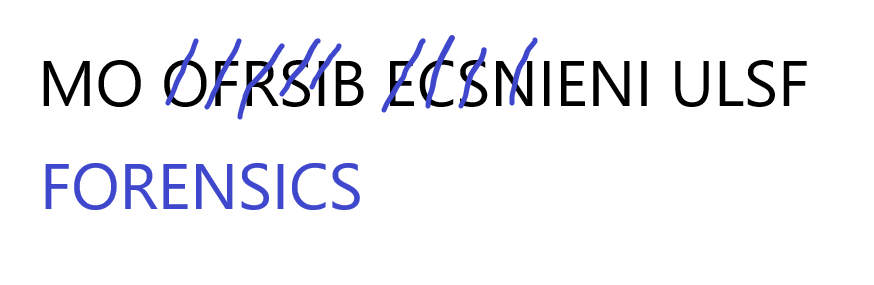2024 Magnet Virtual Summit CTF Walkthrough
This post is a walkthrough of challenges from the 2024 Magnet Virtual Summit CTF.
Background
The 2024 Magnet Virtual Summit CTF, powered by Hexordia, took place on March 6th, 2024. I placed first this year! Congrats to my fellow winners, dumbo (2nd place) and Cognitor4n6 (3rd place). First to finish was Yandao.
Special thanks to the creators of this CTF!
| Name | |
|---|---|
| Alayna Cash | https://www.linkedin.com/in/alayna-cash/ |
| A’zariya (Zari) Daniels | https://www.linkedin.com/in/a-zariya-daniels/ |
| Jessica Hyde | https://www.linkedin.com/in/hydejessica/ |
| Natan Eliezer | https://www.linkedin.com/in/natnan/ |
| James Nicholls | https://www.linkedin.com/in/jnichollscyber/ |
| Derek Farrell | https://www.linkedin.com/in/farrellderek/ |
I had the honor of helping create the 2021 MVS CTF, just participating in 2022, and placing third in 2023. Since the mighty stark4n6 did not participate this year, I thought I would post a walkthrough of how I got flags. I also did not get to finish the CTF during the time allotted , so this gives me an opportunity to go through all the challenges as well.
The following post details on how I personally got the flags. Any flags I got during the CTF allotted time will be marked with a *. Remember, there are tons of ways to get to an answer in a Capture the Flag competition, and this post will not detail all of those, just how I got them.
Image & Device Information
| File Name | Description | MD5 | SHA256 |
|---|---|---|---|
| 00008110-000925383620A01E_files_full.zip | iOS Image | 56ebd62968d37b67e656ad58eee7a985 | 4bf34353e6c13c35ed9ad3d0a5cbae87e1407775d56f6434956326ff4017974b |
| 00008110-000925383620A01E_password.text | Passwords for iOS Image | cd7c935533d5b9c992449cb73b02f4fa | f9767906bf1aef77f7f7f56d6f29b2aeee340faa4317c3440832565a3ca633df |
| 00008110-000925383620A01E.pdf | VeraKey report | 67ca6e66a0278efbe8c291366a0d6f99 | b3c939f6a777f077102ab3b22c649f60b7628214fc3debd39e7e3e37f4a39cbf |
| 00008110-000925383620A01E_keychain.plist | iOS Keychain file | cb493ac5d585e52e4dd0ca75f1af071c | 818d3cd0a734f5adfa6fd3e53f874bb6a457c5ed7e4e6bb9c433bdc8a0aae39e |
| Google Pixel 3a XL Logical Image - Data.tar | Android Image | 11b304c12314d2ce35219cab0c98569e | 1c37b9b932688e9d6b27dd4c24d1cd21f5d0fd081bbf85ab5fad5a0cf2e7c146 |
| Discord.zip | Discord data export | a44036dd301a916cbbd95eb334885357 | 1ba4e558378891c3b3955f323cd7a9f4cf39123cfb4d7af1f4d535626e8f4ccf |
| facebook-61554919820462-2024-01-06-49fzodcA.zip | Facebook data export | b370d4c888225c6418fdd1ffbd83582c | d6f202d965127956769aeae31d234219c49f1f368549a5d1f1f5fe3171c601d6 |
Tools Used
- AXIOM v7.10.1.39284
- iLEAPP v1.18.10
- aLEAPP v3.1.10
- DB Browser for SQLite
- exiftool v12.78
iOS
All flags were found using the 00008110-000925383620A01E_files_full.zip image, for this section.
The following flags were not found (yet) for iOS and will be updated when they are:
- Its been a long time
- The devil is in the details
Why are your messages green? (5 points*)
On what date did Rocco and Chadwick first meet in person according to their conversations? YYYY-MM-DD format
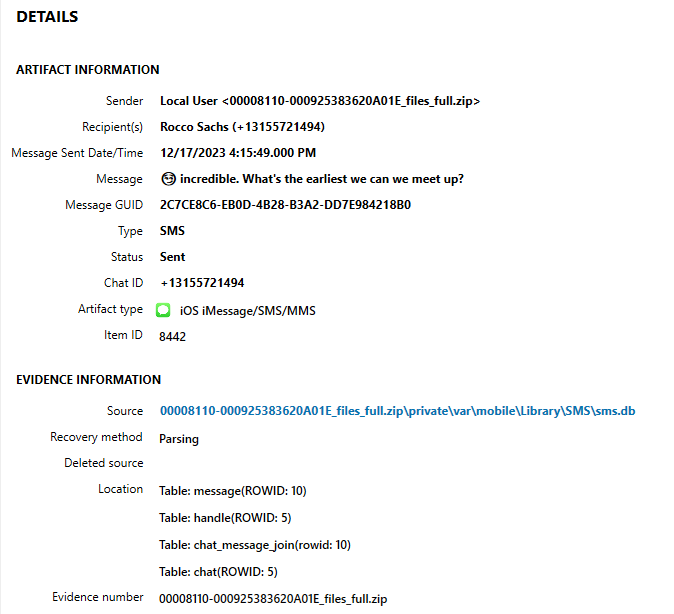
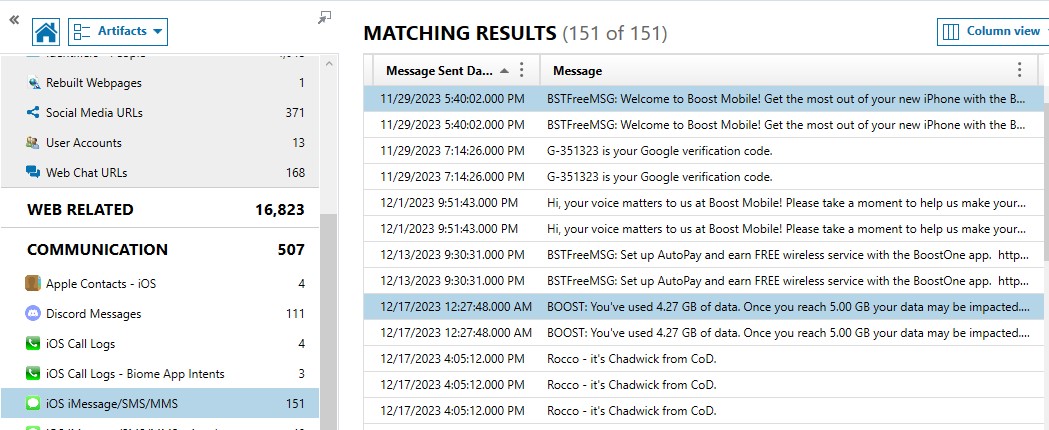
The challenge is asking for a date based on conversations. Based on the title, this will most likely lie within the iOS message artifacts. Using AXIOM, I navigated to the “COMMUNICATION” section, and selected “iOS iMessage/SMS/MMS”. Within this section, I quickly scanned through conversations until I found one with Rocco. From the VeraKey report, we know the owner of the phone is named “Chadwick Elms”, so this conversation will be from the device to Rocco.
The only time Rocco and Chadwick messaged about meeting in person was on 12/17/2023. As seen in Figure 1.1, this message can be found at the filesystem location ‘\private\var\mobile\mobile\Library\SMS\sms.db’.
Message 10 asks when the earliest that they can meet up. Based on other messages in the same message chain, the meetup did happen that same day. 12/17/2023 just needs to be formatted to YYYY-MM-DD, and that is the flag.
- flag
- 2023-12-17
Where /r u going on safari? (5 points*)
What subreddit was visited in a browser?
In the question, safari is mentioned, pointing us in the direction of Safari artifacts. Since all reddit URLs include the word “reddit”, I did a keyword search in AXIOM, and then looked at the “WEB REALTED” section, and selected “Safari History”. Reddit URLs denote the subreddit page after the “/r”. As seen in Figure 1.2, all results for the keyword search “reddit” on Safari history included “/r/Twitch”, meaning the subreddit visited was the Twitch subreddit. 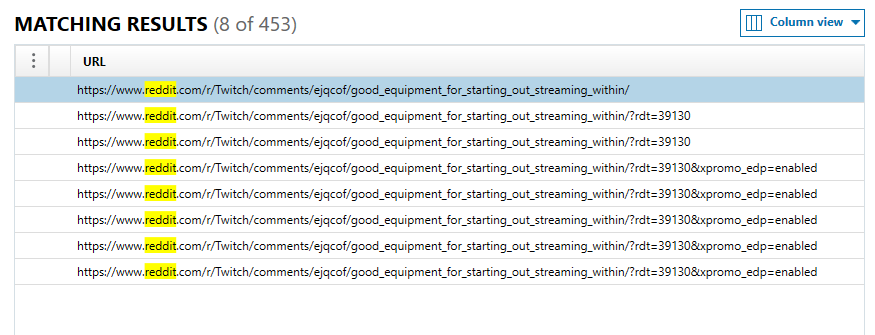 Figure 1.2
Figure 1.2
- flag
- Twitch
IMAGEine living in pain (5 points*)
Chad seemed to be searching for pain relief medicine in a store, how much did it cost?
This one took me a hot sec, as I jumped right into keyword searches before actually paying attention to the question itself. IMAGE is capitalized, hinting that the flag will be found in a photo. Under the “MEDIA” section in AXIOM, I looked under the “Photos Media Information” tab. I looked here instead of “Pictures” as it just includes information for pictures and videos found within the native iOS “Photos” application, making it more likely the user took these photos. I scrolled through until I found “IMG_0017.HEIC”. The photo, found at the file system path “\private\var\mobile\Media\PhotoData\Thumbnails\V2\DCIM\100APPLE\IMG_0017.HEIC”, was a picture of pain relief gel, along with a price tag, as seen in Figure 1.3.
- flag
- 10.99
Your keyboard is salt-y (5 points)
How many total words were typed on the device?
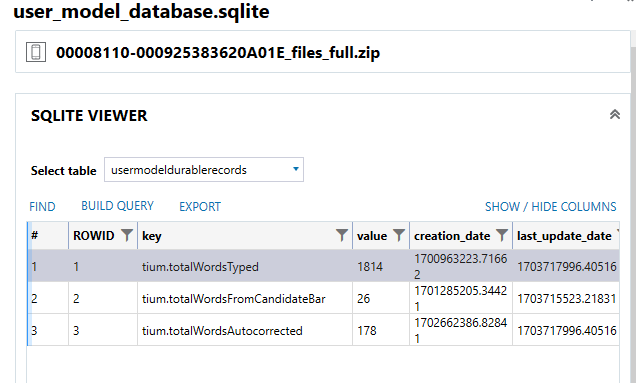
I am surprised I could not get this flag during the CTF time, as it was only 5 points (and those tend to be easier). I had quickly done some research on where this information is stored on iOS, but could not find the flag during the allotted 3 hours. I had the right article, but the heat of battle did not get me to the right database in time. BUT the smoke has settled, and the flag can be found at the path: “private\var\mobile\Library\Keyboard\user_model_database.sqlite”, in the table “usermodeldurablerecords”. In that table, the key “tium.totalWordsTyped” holds the flag value, as seen in Figure 1.4. I used AXIOM’s native SQLITE Viewer for this, but any SQLite viewer could be used.
The information on artifact location was found via the blog Salt4n6 https://salt4n6.com/category/mobile-forensics/.
- flag
- 1814
Answer the call (5 points*)
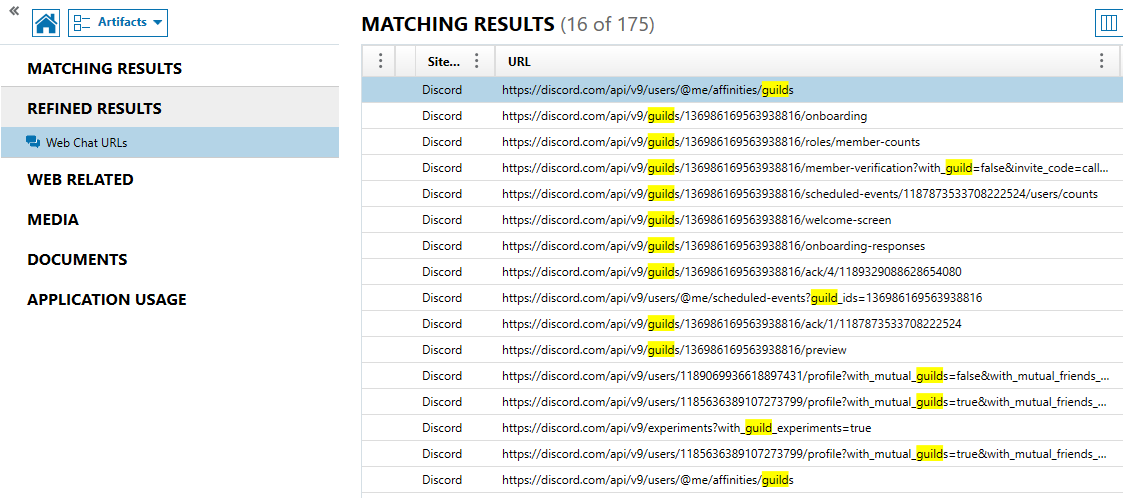
What is the guild ID of the discord server Chad was in?
In AXIOM, I did a keyword search for “guild”. In the “REFINED RESULTS” section, the subsection “Web Chat URLs” parsed out quite a few discord links. Most of these had the guild ID in the URL, immediately following “/guilds/”. The most common link base was “https://discord.com/api/v9/guilds/136986169563938816/”, as seen in Figure 1.5.
- flag
- 136986169563938816
Don’t ghost me (5 points*)
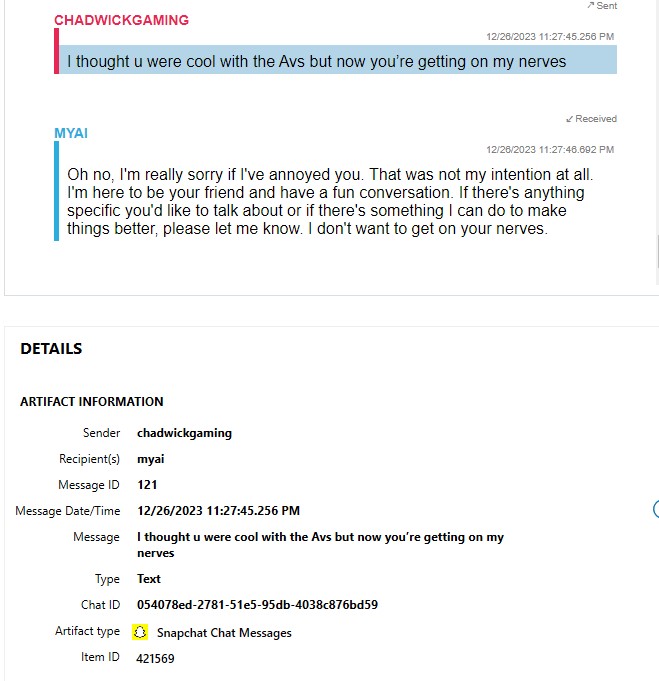
At what time did Chadwick get annoyed at MYAI? YYYY-MM-DD HH:MM:SS UTC
MYAI is a feature of Snapchat. Since I know this, I will go directly to Snapchat artifacts in AXIOM, but a quick keyword search of “myai” would get you there as well. In the conversations between Chadwick and MYAI, MYAI apologies for annoyed Chadwick. The message before that is “I thought u were cool with the Avs but now you’re getting on my nerves”, sent at 12/26/2023 11:27:45.256 PM UTC, as seen in Figure 1.6.
The format of that date to the flag format is 2023-12-26 23:27:45 UTC.
- flag
- 2023-12-26 23:27:45
Build me up, buttercup (5 points*)
What is the current build version?
The artifact containing information on build version can be found at the location “\private\var\installd\Library\MobileInstallation\LastBuildInfo.plist”. This information is nicely parsed out by iLEAPP, under the IOS BUILD section, as seen in Figure 1.7, and is Build 20F75. 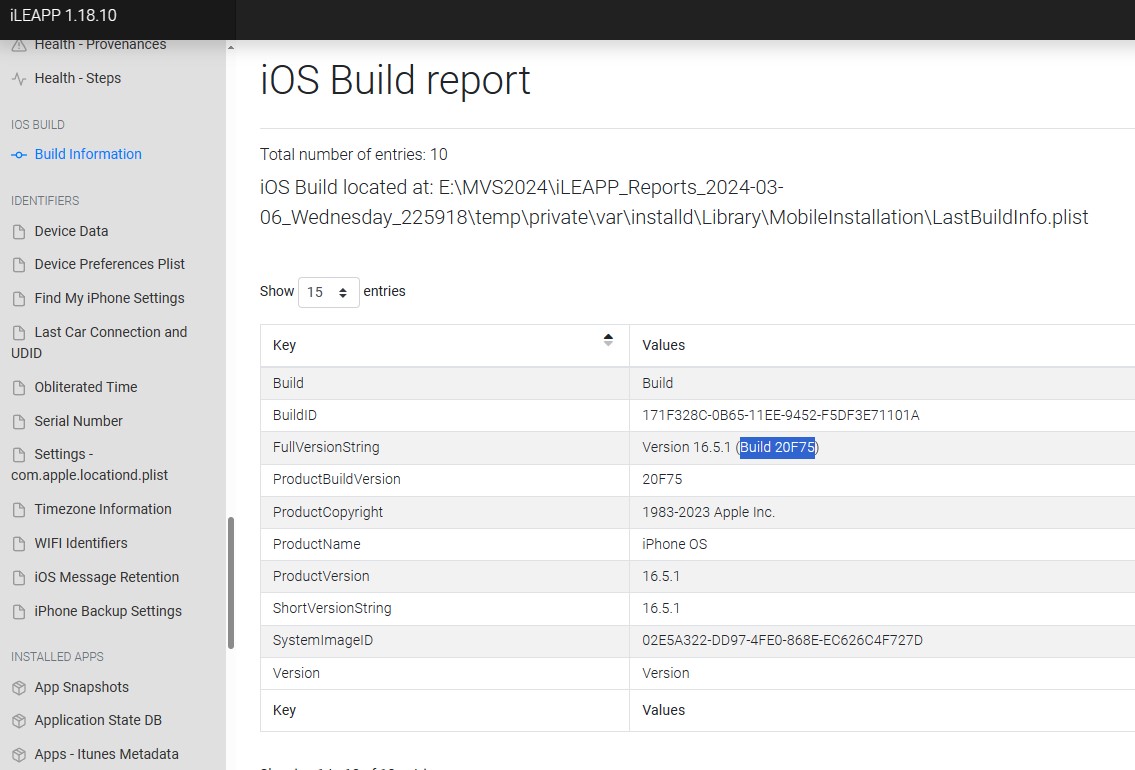 Figure 1.7
Figure 1.7
- flag
- 20F75
Warning Signs (5 points*)
How many days did it take Chad to be warned about his Data Usage?
Data usage warnings normally come through notifications or text messages. In AXIOM, I went to the “COMMUNICATION” section, and the iOS “iMessage/SMS/MMS” subsection. I then ordered the dates from oldest to newest. Messages welcoming Chadwick to Boost mobile were first received on 11/29/2023. On 12/17/2023, the first message warning about data is received, as seen in Figure 1.8. This is 18 days since the plan started.
Text message artifacts are logged at the location “\private\var\mobile\Library\SMS\sms.db”.
- flag
- 18
Watching streams to stay current (10 points)
What is the name of Chad’s streaming channel?
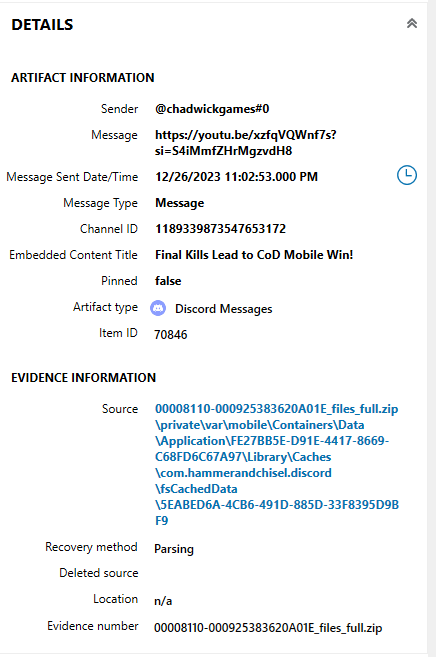
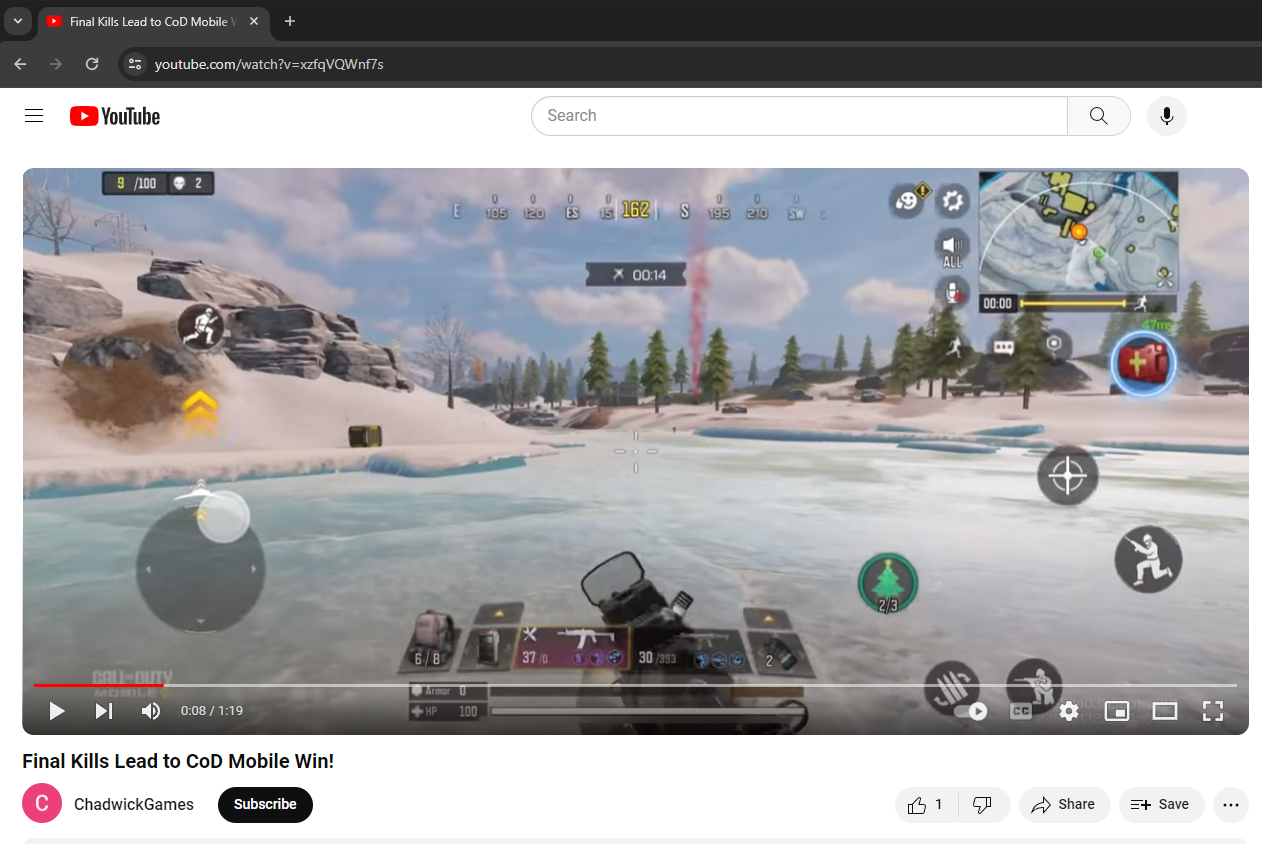
Normally, gamers either stream on Twitch or YouTube. Gamers also often use Discord. I first tried keyword searching for Twitch, and did not find much. I then looked through Discord Messages under “COMMUNICATION”. When scrolling through, I noticed a few messages that mentioned streaming. I also found a message with a YouTube link in it. I did not see any other YouTube links, so I copied the link found, seen in Figure 1.9.1, into a web browser (“https://www.YouTube.com/watch?v=xzfqVQWnf7s”).
As seen in Figure 1.9.2, this a streaming video posted by ChadwickGames.
- flag
- ChadwickGames
What question did Chadwick ask to AI? (10 points*)
What question did Chadwick ask to AI?
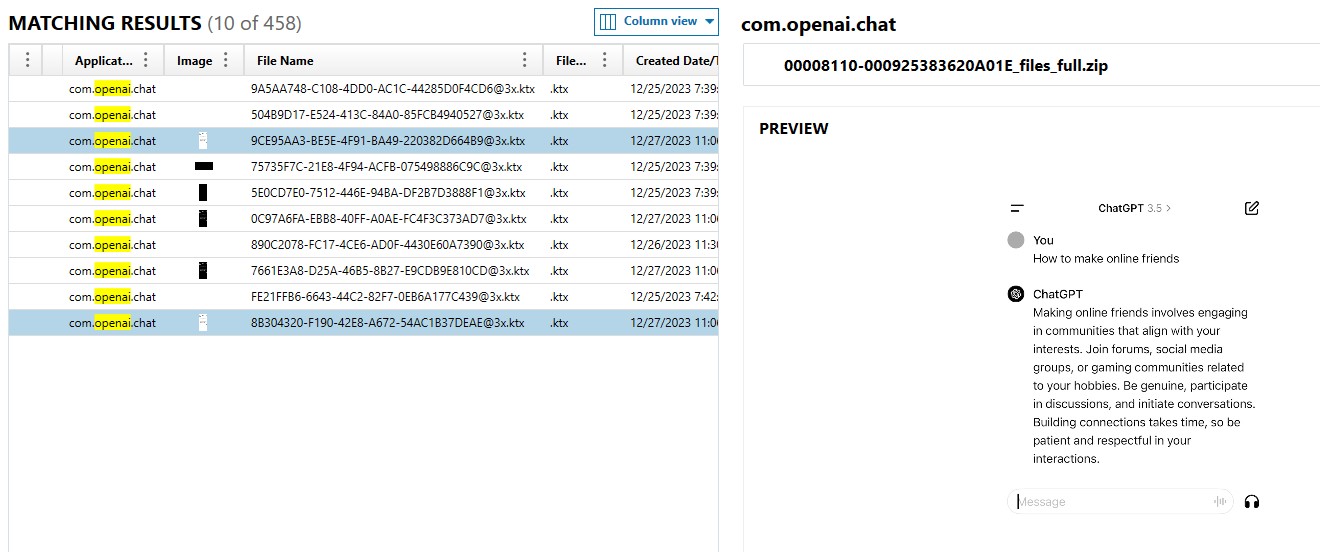
After attempting to put every question that Chad asked myAI on Snapchat, I knew there must be another AI service used on the phone. The most popular AI at the time is ChatGPT, made by OpenAI. Searching for “ChatGPT” in AXIOM came with no relevant results, other than confirming that the ChatGPT app was installed on the phone. The package name is “com.openai.chat”, so I attempted to search for “openai” next.
In these results, I could see that there were 10 iOS Snapshots taken within the application “com.openai.chat”, under the Media section. Two of those snapshots include the same content, of the question “How to make online friends” being asked, as seen in Figure 1.10.
- flag
- How to make online friends
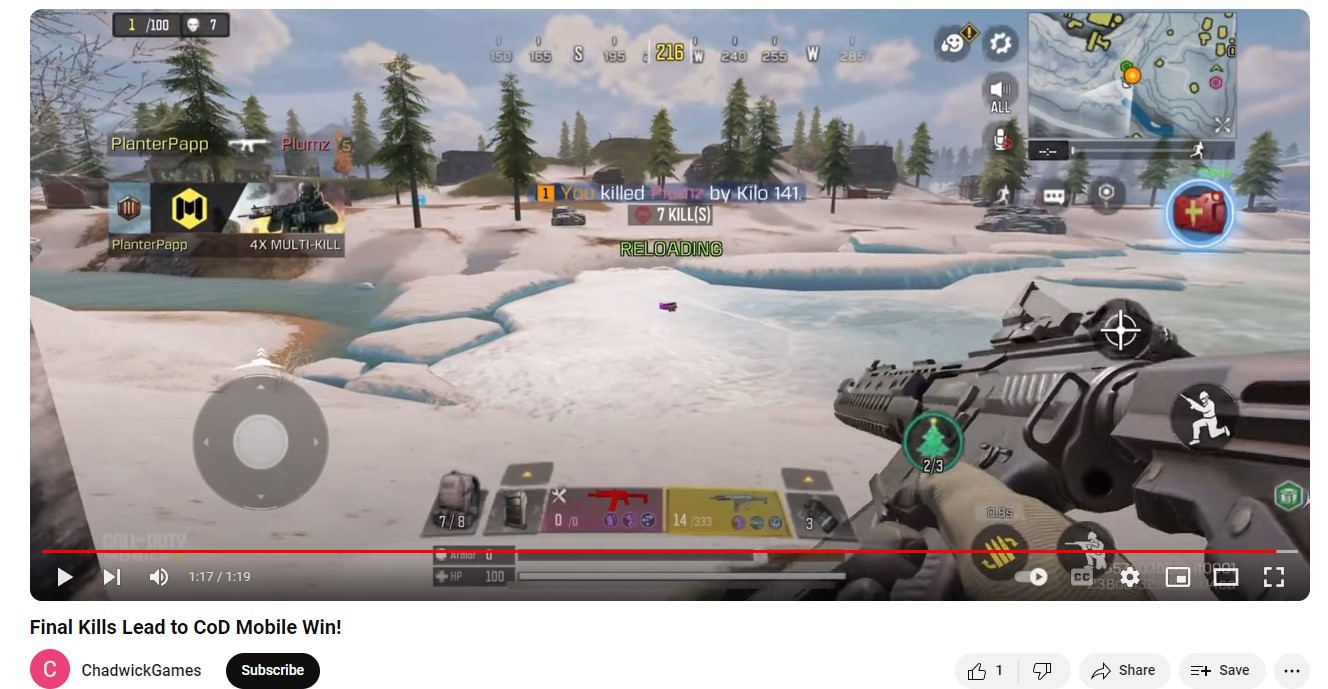
Watch me sUAVely win this game (10 points*)
How many kills did Chad have on his CoD Mobile winning game? A winning match was most likely being recorded by Chad, who was trying to get into streaming. Under the “MEDIA” section in AXIOM, I first looked under “Photos Media Information”. I went through the videos found here, and found a few recorded of the COD (Call of Duty) mobile app. Scores for COD games tend to be shown at the end, so I skipped to the end of the video where “WINNER” was shown, and went back about 30 seconds. A few matches recorded were winners, but there was one I found (“IMG_0041.MOV”) that had Chad making the final kill, bringing his score up to “7”. This video matches the one posted to YouTube by Chad, the same mentioned in “Watching streams to stay current”. As seen in Figure 1.11, this video shows the score by Chad at 1:17 seconds.
Starting here probably would have been easier….
- flag
- 7
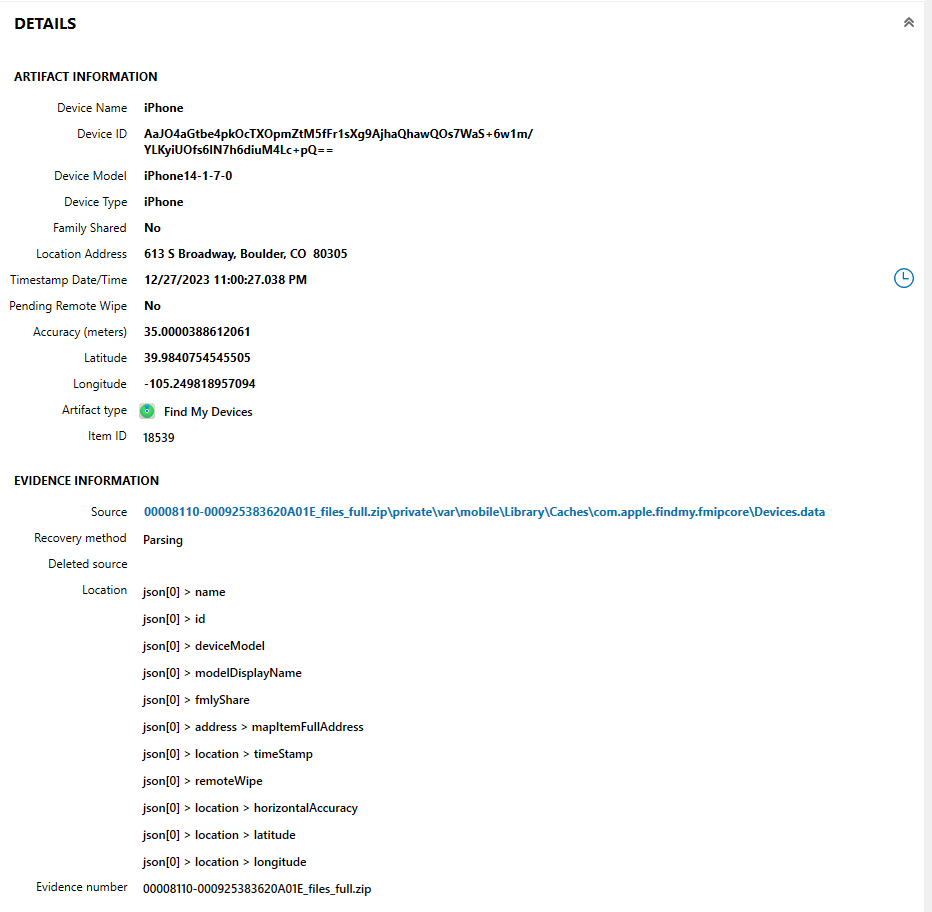
For when I cant Find My gear (10 points)
What outdoor activity store did Chadwick Visit?
I really thought this answer lay in the photos and maps locations on the devices, which mentioned the store ‘Christy Sports’ many times. ‘Christy Sports’ was eventually accepted as an alternate flag. But again, I missed a challenge name clue. Find My is so obviously capitalized, I am not sure how I missed it the first time around. Regardless, the hint points in the direction of Find My artifacts, shown under the “CONNECTED DEVICES” section in AXIOM. Under “Find My Devices”, there is one entry that has an address associated with it. That address is 613 S Broadway, Boulder, CO 80305, as seen in Figure 1.12.
A quick google search led me to Maps, which showed the store “Neptune Mountaineering” as at this address.
- flag
- Neptune Mountaineering
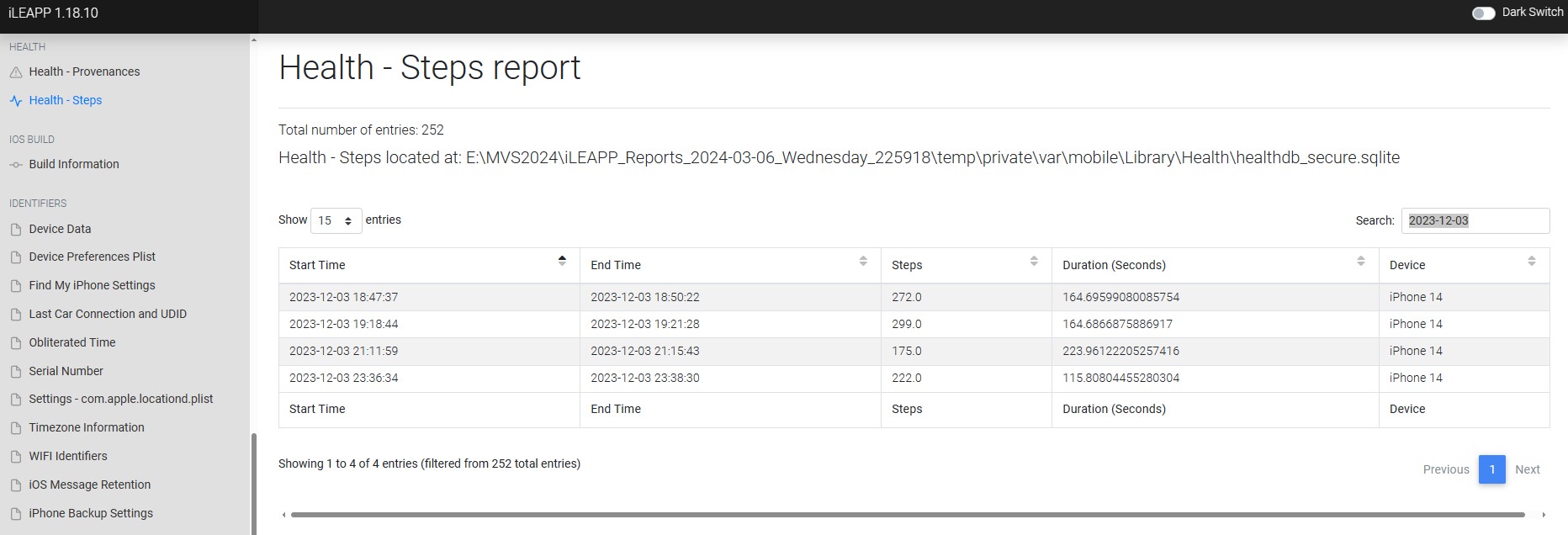
Just a couple steps away (10 points*)
How many steps did Chad take on 12/3/2023?
In iLEAPP, I went to the “HEALTH” section, and subsection “Heath - Steps”. I filtered to “2023-12-03” by searching that date, where there were 4 entries, as seen in Figure 1.13. I added up all the entries (272 + 299 + 175 + 222) to get a total step count of 968.
- flag
- 968
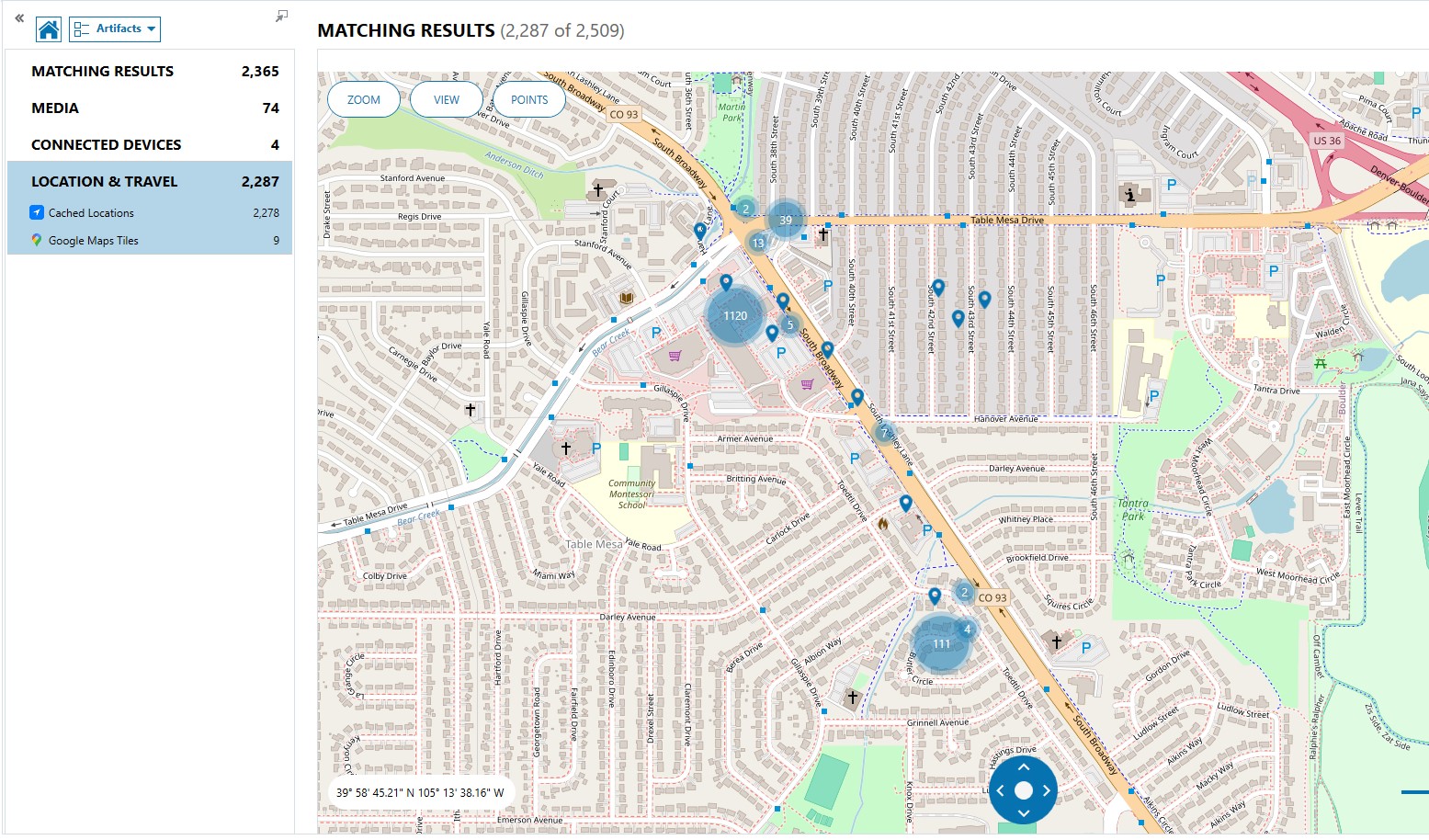
Another regularly scheduled program (10 points)
What Tattoo shop was visited on 12/27/2023?
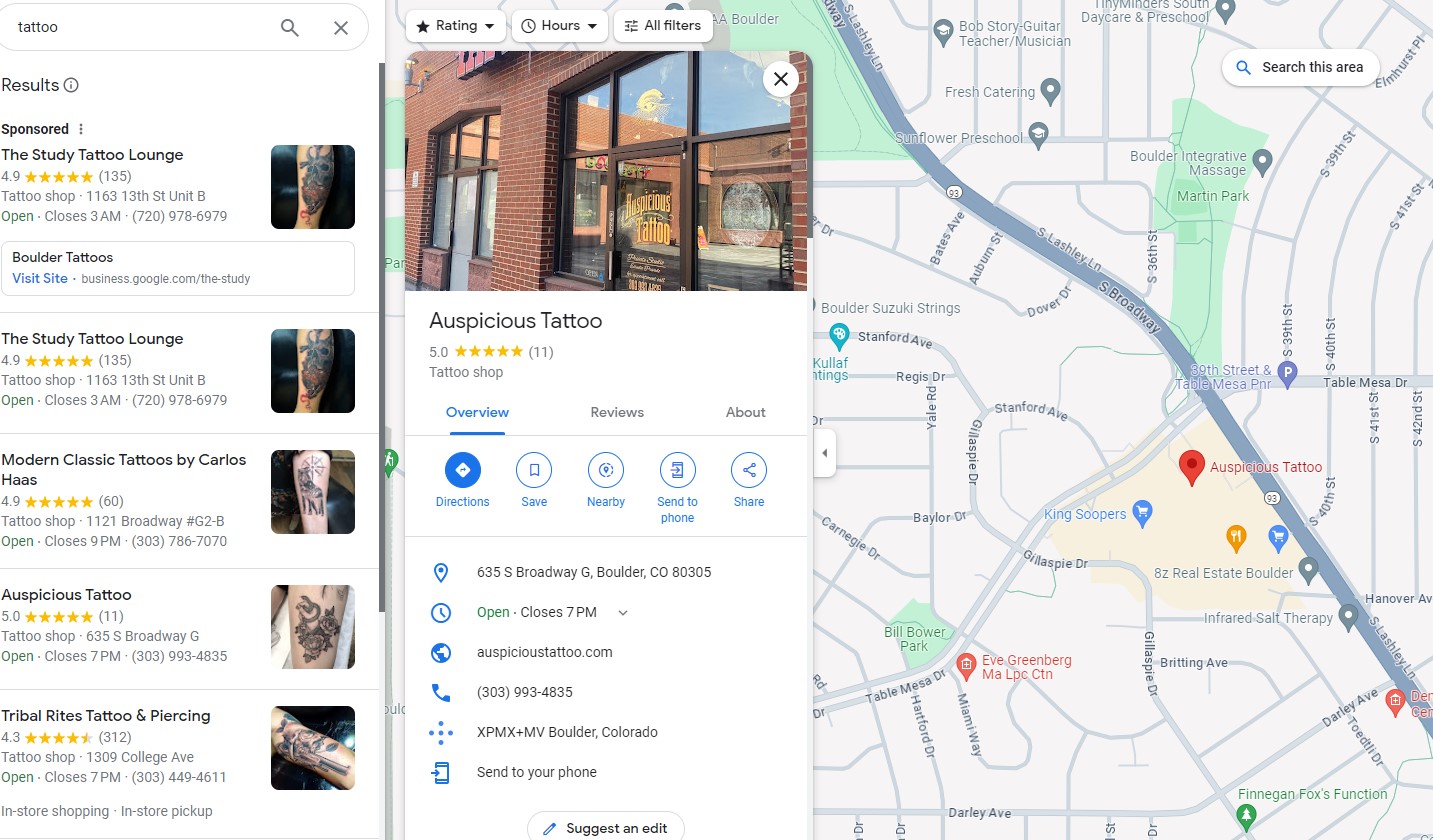
In AXIOM, I looked at the “LOCATION & TRAVEL” section, all artifacts. I filtered on the “Accessed Date/Time -UTC” column for 12/27/2023. I then went to World Map view, and zoomed in on the greatest concentration of results. These results were concentrated in Boulder, CO, USA, specifically on the road “South Broadway”, as seen in Figure 1.14.1.
I then opened Google Maps and searched for “s broadway boulder co”. I zoomed out a bit to get a better view, and then searched “tattoo” in that area. The only tattoo shop that showed up on Broadway was “Auspicious Tattoo”, as seen in Figure 1.14.2. and then the “cached locations” subsection.
- flag
- Auspicious Tattoo
I hear Stanley cups are all the rage (25 points*)
What was the final score of the hockey game Chad went to? (home-away)
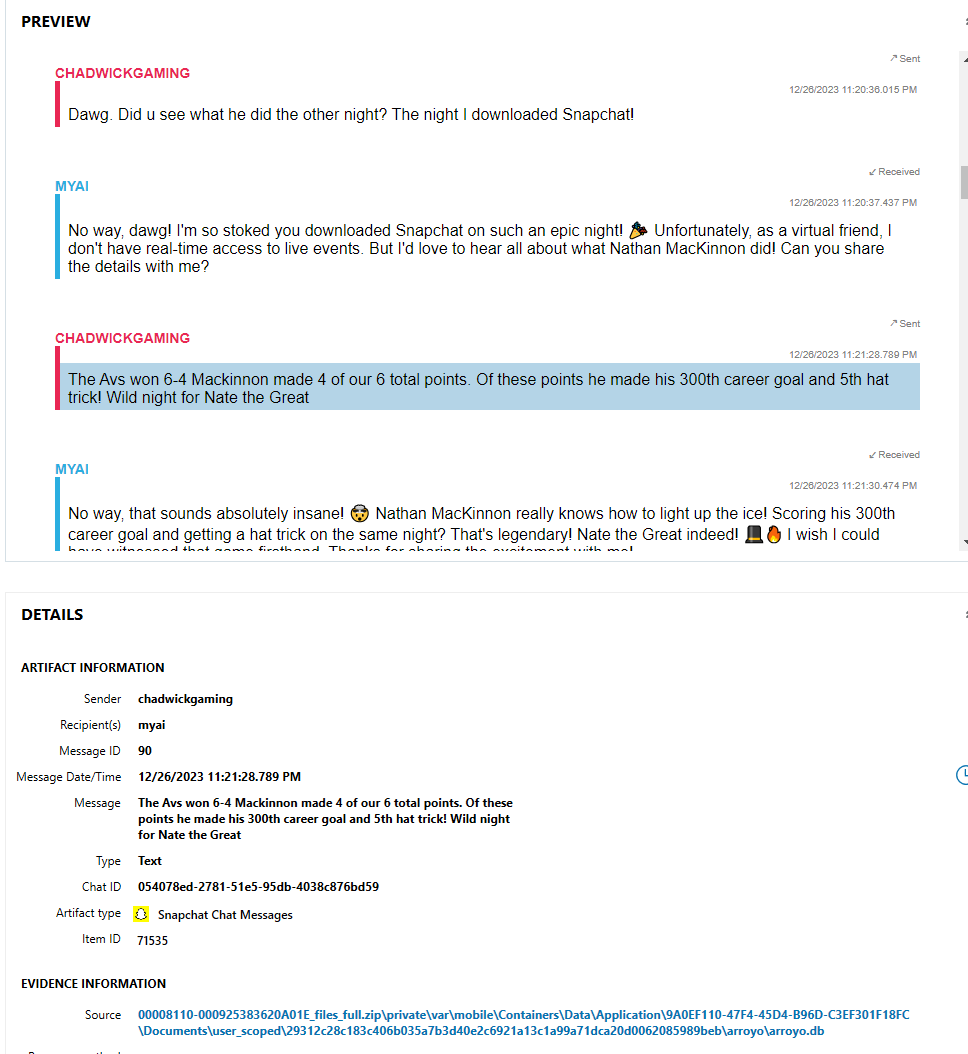
From previous challenges, I remembered that Chadwick had talked about Hockey with the MyAI account in Snapchat. In AXIOM, I went to the “COMMUNICATION” section, and “Snapchat Chat Messages”. In those messages, Chadwickgaming sent a message to MyAI on 12/16/2023 at 11:21 PM UTC saying that in the hockey game he attended, the AVS won 6-, as seen in Figure 1.15.
- flag
- 6-4
Exuse Moi? What did you say? (25 points*)
What is the content of the 2nd message that Chad deleted on Dec 18, 2023
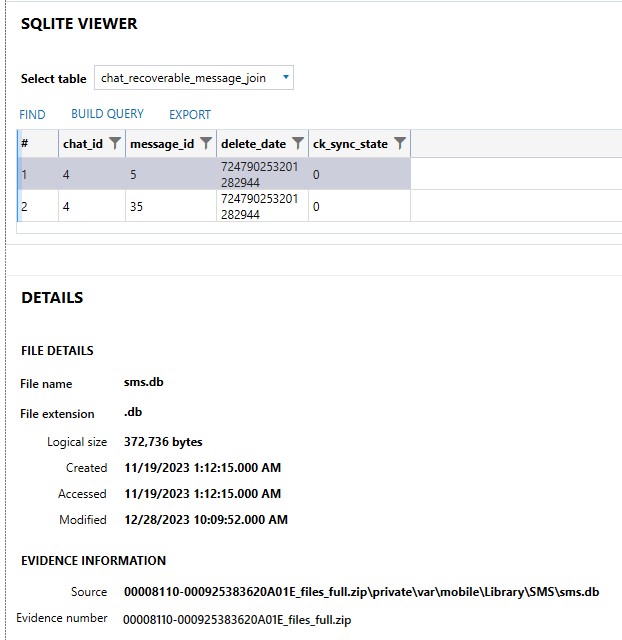
This one stumped me for awhile on the day of the CTF. I knew iOS 16 had the feature to unsend/delete messages, and that for 30 days, those still show up in the messages database as being deleted. On the iOS image, I found where two messages were marked as being deleted in the “\private\var\mobile\Library\SMS\sms.db” file, but I could not find the content for them (Figure 1.16.1)!
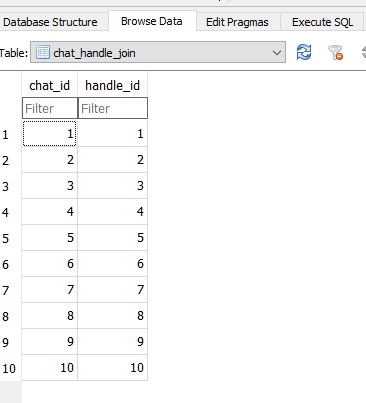
The deleted date was “724790253201282944” and I took note of that. There were also two handle_ids, 5 and 35. In the table “chat_handle_join”, it is shown that “chat_id” and “handle_id” match for values shown (Figure 1.16.2).
As the second message deleted was to Rocco, I decided to look on the Android image for evidence, since unsent/deleted messages only work between iOS 16 devices. I sorted by Received Date/Time, and looked at messages on 12/18/2023. There were three messages that do not match values found in the “message” table in the iOS “sms.db” file, matching the chat_id 5.
These were: “Let’s meet there at 9pm in 26min” “Excuse me?! That’s quite a bold statement considering I’m the one who walked away with a black eye and spent $30 last night on products to avoid one!” “I’ll even throw in a third one for free just for you”
The second message on 12/18/2023 is the flag.
- flag
- Excuse me?! That’s quite a bold statement considering I’m the one who walked away with a black eye and spent $30 last night on products to avoid one!
Its been a long time (25 points)
When did chad last login to Facebook? YYYY-MM-DD HH:MM:SS UTC
I was not able to complete this challenge yet.
Can anyone Kelp? (25 points*)
What game was Chad asking to know the strategy to?
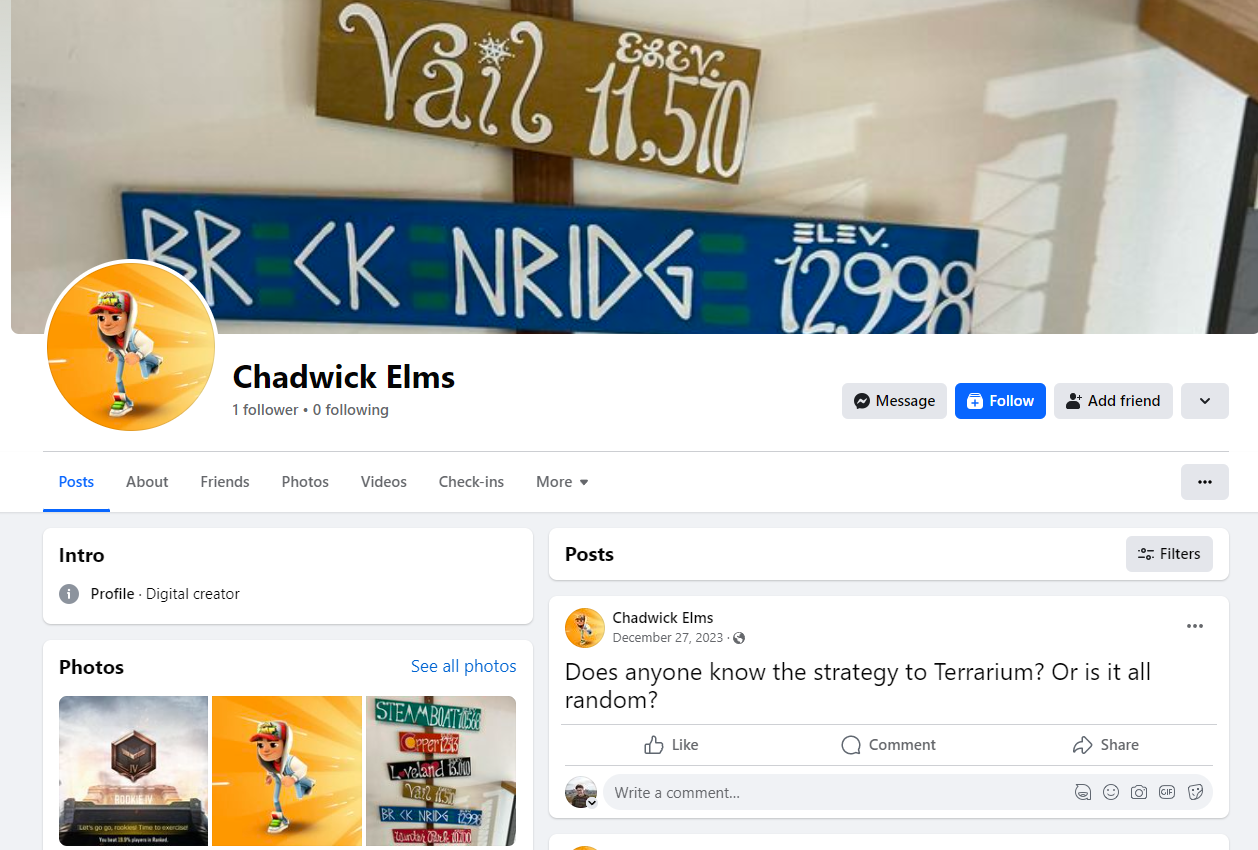
Chad liked gaming - any game. At first this was hard to narrow down, as I did not see any results for “strategy” or the like for keyword searches in AXIOM. Since I knew Chad had a Facebook, I just looked up his profile. There, he had made a post about the strategy to Terrarium, as seen in Figure 1.18.
- flag
- Terrarium
The devil is in the details (25 points)
Whose bitmoji is dressed like a devil?
I was not able to complete this challenge yet.
The easy way or the hard way (25 points*)
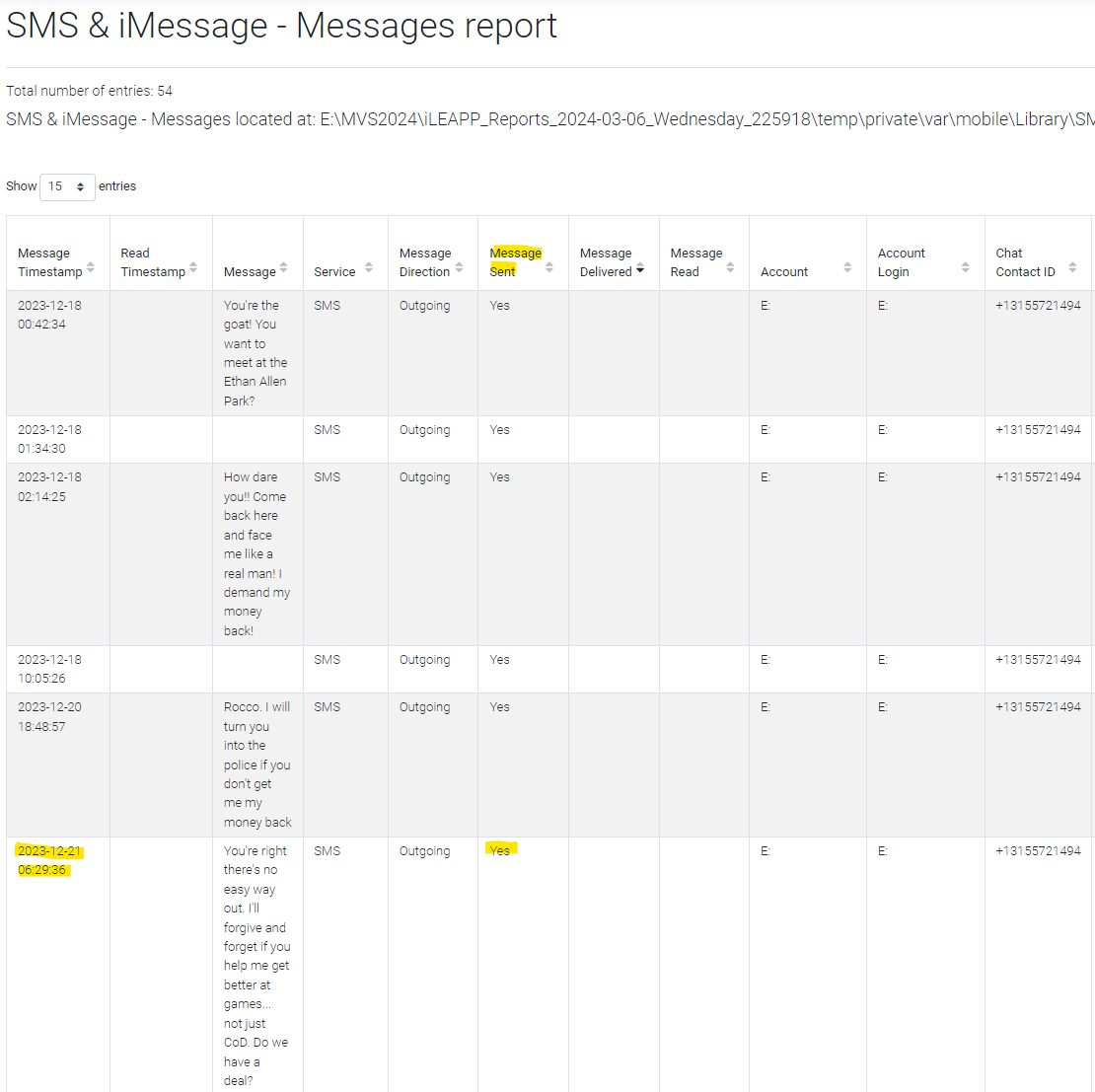
What is the timestamp of the message Chad sent to Rocco but was never received? YYYY-MM-DD HH:MM:SS UTC
Very similar to the method of “Exuse Moi? What did you say?”, I compared the messages on each phone to find this flag, within iLEAPP and aLEAPP. The one message that existed on the iOS device and not the Android was “You’re right there’s no easy way out. I’ll forgive and forget if you help me get better at games… not just CoD. Do we have a deal?”, sent at 12/21/2023 6:29:36.000 AM UTC, as seen in Figure 1.20.
- flag
- 2023-12-23 06:29:36
Follow the Breadcrumbs (50 points)
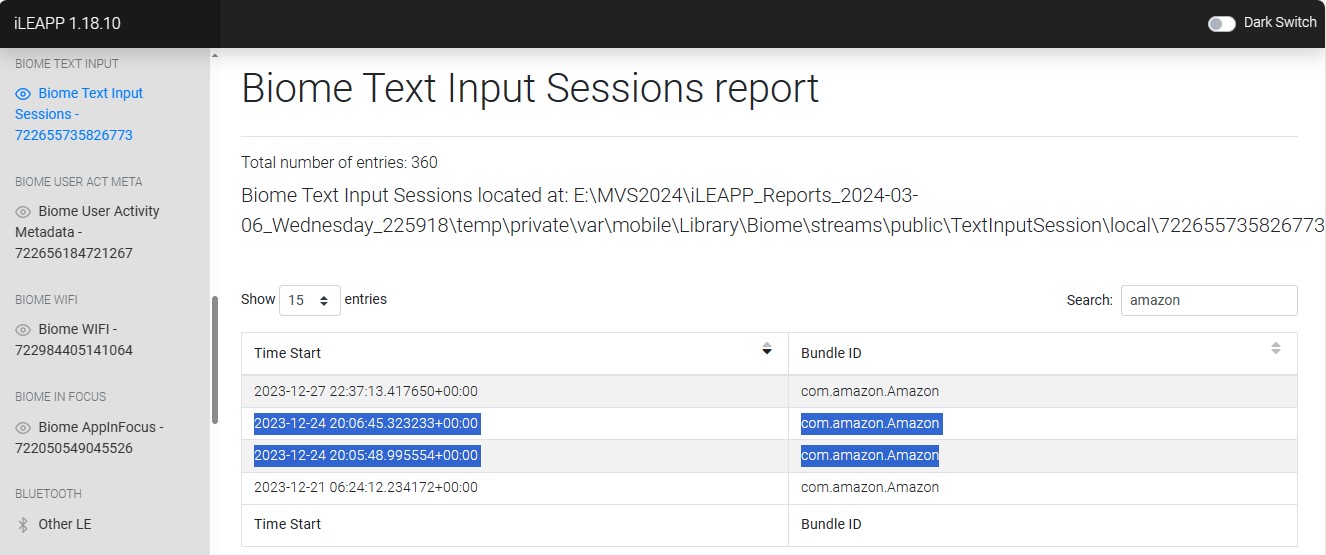
How many times did Chad’s keyboard become visible within the Amazon app on 12/24/2023?
I was not able to find this flag during the CTF time, but did after. During the CTF, I was looking in the right place, but could not seem to find the information with using AXIOM alone. In iLEAPP, the “BIOME TEXT INPUT” section holds the answer to this challenge. Within this report, I searched for “amazon”. This narrows things down to four entries for amazon, only two of which occur on 12/24/2023, as seen in Figure 1.21.
The location on the iOS for this artifact is “private\var\mobile\Library\Biome\streams\public\TextInputSession\local\722655735826773”
- flag
- 2
Read my mind (50 points*)
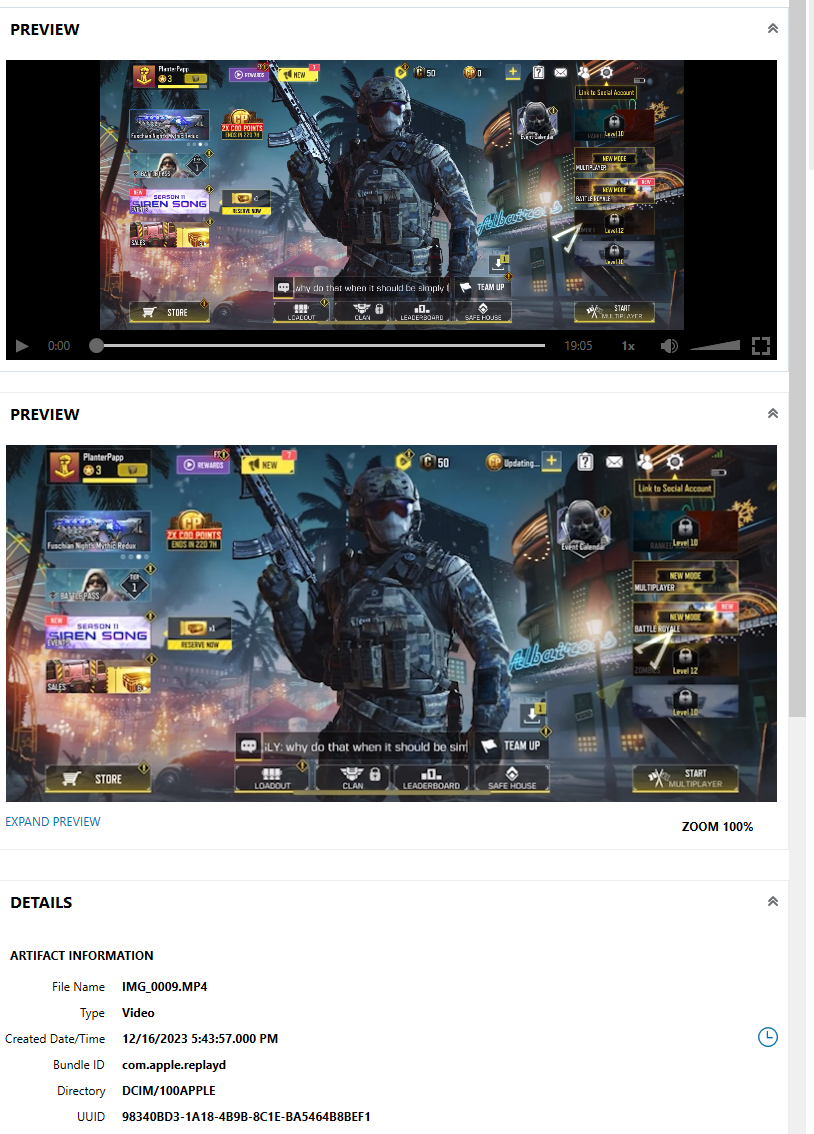
What message was sent to Rocco in a video game?
Earlier in the CTF, I remembered seeing a screenshot of a chat windows in the “MEDIA” section in AXIOM, under “Photos Media Information”. The preview of “IMG_0009.MP4” shows a message being sent in CoD that shows up as “why do that when it should be sim…”, the last word completing to “simply”, seen when playing the video, as seen in Figure 1.22.
All photos and videos are listed in the database “\private\var\mobile\Media\PhotoData\Photos.sqlite”, the specific location of the video being at “\private\var\mobile\Media\DCIM\100APPLE\IMG_0009.MP4”.
- flag
- why do that when it should be simply
Chat GPT is my PREFERENCE for AI (50 points*)
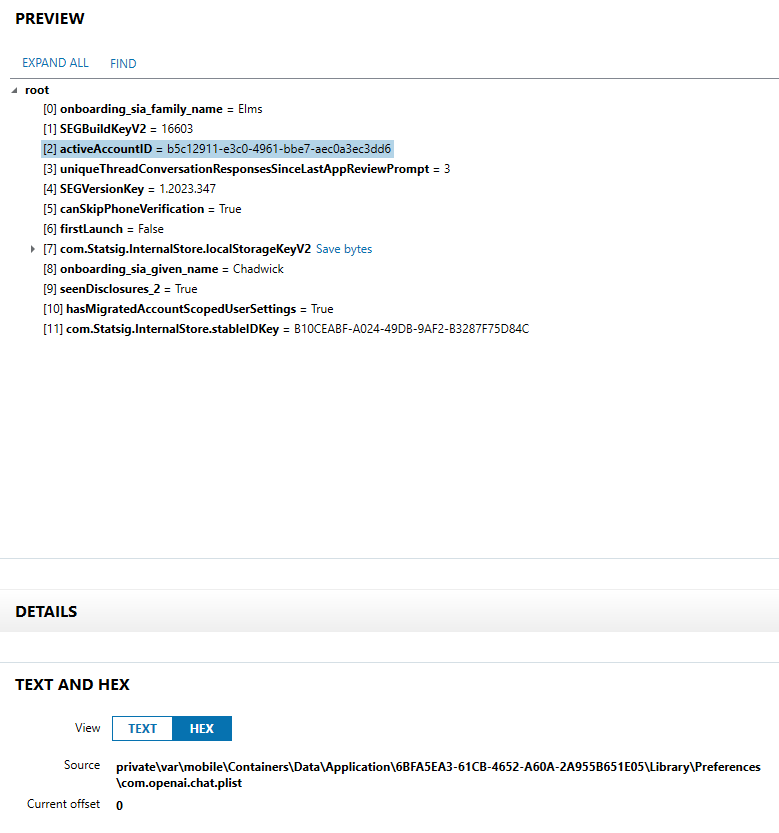
What is the ChatGPT userID associated with chadwickmr95@gmail.com
Knowing that ChatGPT is made by the company OpenAI, I keyword searched “openai” in AXIOM. I was able to narrow down the app data folder under information within the “APPLICATIONUSAGE” section under “Installed Applications”, which was “private\var\mobile\Containers\Data\Application\6BFA5EA3-61CB-4652-A60A-2A955B651E05”. I navigated there using the file system explorer within AXIOM, where I poked around the various plist and db files within the ChatGPT app folder. Under the subfolder “\Library\Preferences\com.openai.chat.plist”, I ran into an entry named “activeAccountID” that had a value of “b5c12911-e3c0-4961-bbe7-aec0a3ec3dd6”, as seen in Figure 1.23.
“Chadwick” was listed as a first name and “Elms” as a family name, so I figured there was a strong possibility that this was the flag.
- flag
- b5c12911-e3c0-4961-bbe7-aec0a3ec3dd6
Season’s Greetings (75 points*)
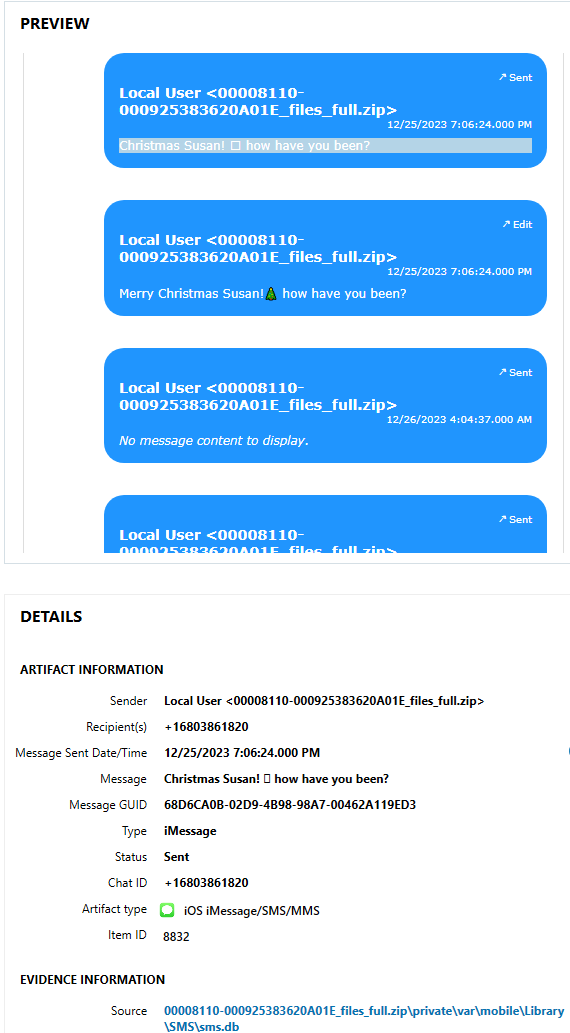
What was the name of the first emoji that was sent to Susan?
Emojis are usually sent over text, so I went straight to the “COMMUNICATION” section, “iOS iMessage/SMS/MMS” subsection in AXIOM. On 12/15/2023, Chad sent a few messages to Susan, known by him addressing the recipient as Susan in the messages. The first message includes an emoji that is shown with a box symbol, and an edited version of that message with a Christmas Tree emoji, as seen in Figure 1.24.1. This same information could be found in the “sms.db” file found at “\private\var\mobile\Library\SMS".
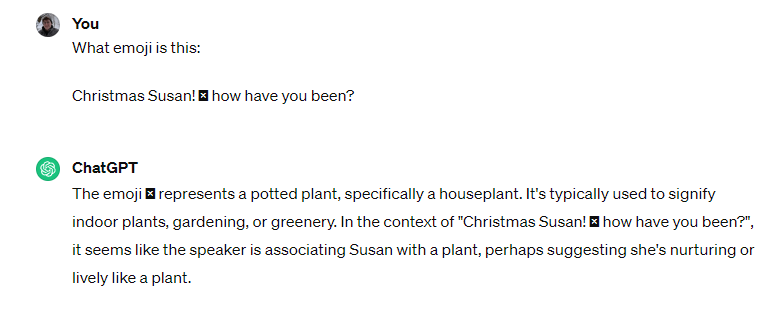
No information in the “sms.db” database depicted a code or description for the first emoji. Upon some googling, I found that there are emoji decoding tools online! I do not remember the exact emoji decoder I used during the CTF itself, but to show that tools can translate, I pasted the message into ChatGPT while making this walkthrough to see if it could translate it. As seen in Figure 1.24.2, it did indeed!
The correct answer is “Potted Plant”.
- flag
- Potted Plant
Cipher
The following flags were not found (yet) for Cipher and will be updated when they are:
- BASH these ROTten criminals
- Why did the stego expert wear a ‘cloak’? To keep their messages undercover!
- What is your favorite SHAKESPEARE play?
- ROTten people hiding their secrets!
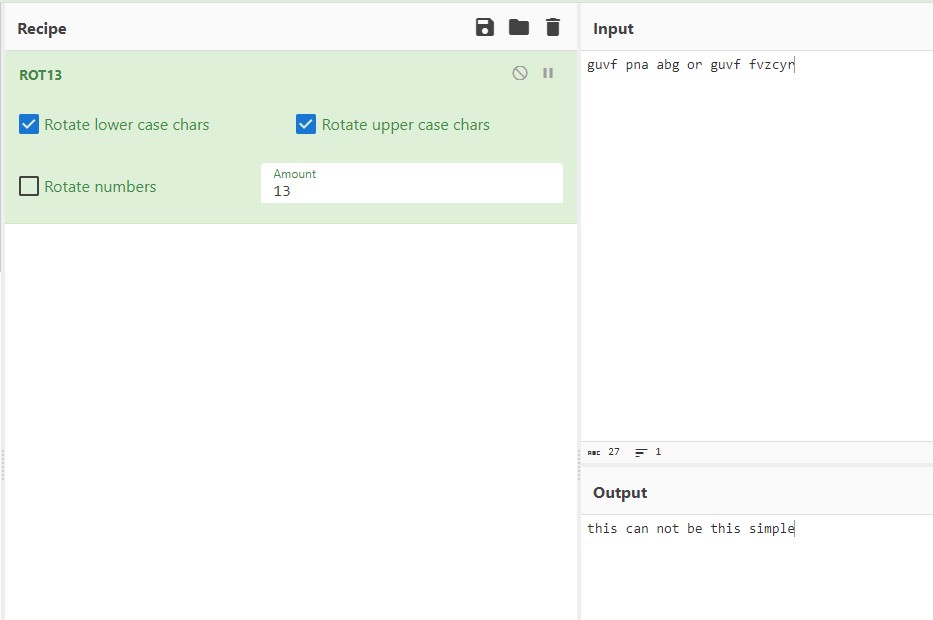
Why did the bicycle fall over? It was tired of all the ROTation! (5 points*)
rfgq ayl lmr zc rfgq qgknjc
The challenge emphasizes ROT, hinting this might be the cipher used. The most common ROT cipher is a ROT13, so I put the cipher into CyberChef and set the recipe to decode from ROT13, which had an output of “this can not be this simple”, as seen in Figure 2.1.
- flag
- this can not be this simple
Have you ever tried reading the alphabet in reverse? (5 points*)
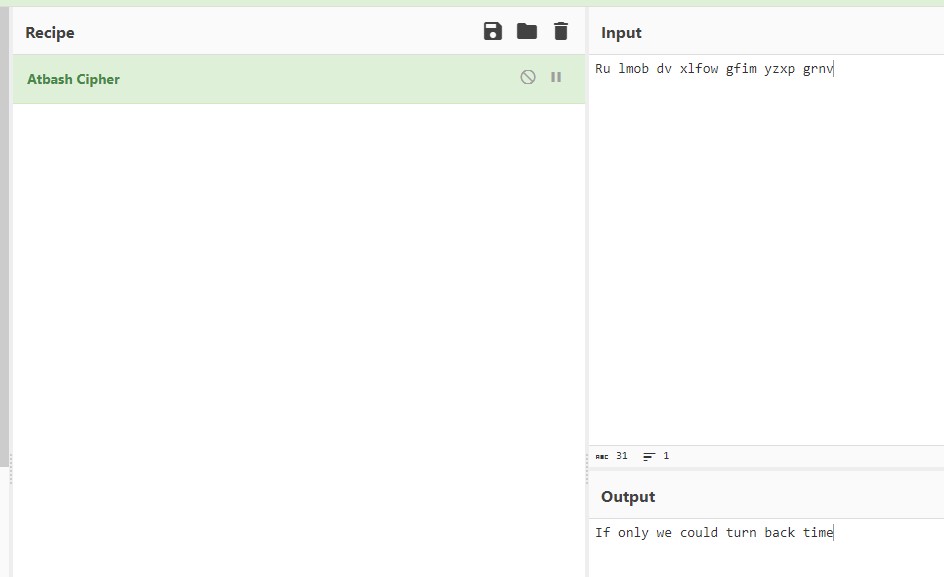
Ru lmob dv xlfow gfim yzxp grnv
“Alphabet” makes me think of the atbash cipher. In CyberChef, I tried inputting the cipher with Atbash as the recipe, and decoded. The output was “If only we could turn back time”, as seen in Figure 2.2, which was the flag.
- flag
- If only we could turn back time
The train joke I wrote didnt gain any traction—it went off the RAIL! (5 points*)
MO OFRSIB ECSNIENI ULSF
“RAIL” as a hint made me think of a rail fence cipher, but I did not get too into that train of thought, as just looking at the cipher I thought I could pick out the words. I thought I could see FORENSICS, so I crossed out all the letters so I could see what was left (Figure 2.3.1).
After eliminating some of the letters, I thought I could see the word “MOBILE” as well (Figure 2.3.2).
After that, there is only five letters left, N I U S F. I see an “IS” within that, with the remaining N U F making “FUN” (Figure 2.3.3).
- flag
- MOBILE FORENSICS IS FUN
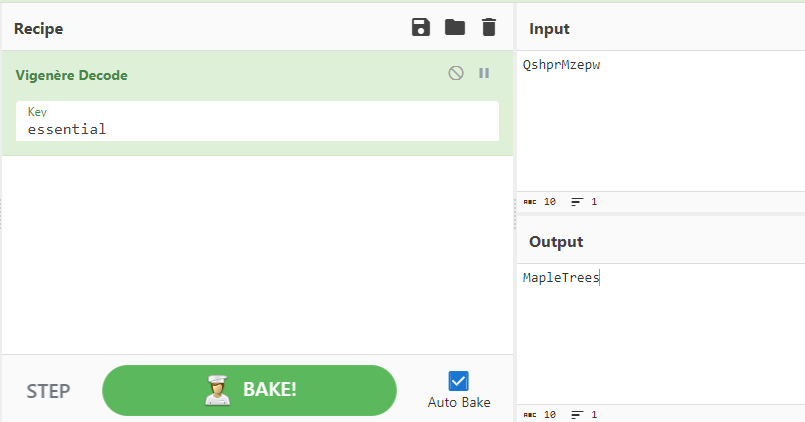
VIGorous ENcrypting? Embrace the Riddle’s Essence, it’s “essential”! (10 points)
QshprMzepw
Each capitalized letter in the challenge name spells of VIGENERE, hinting a vigenere cipher. Vigenere ciphers need a key word, provided by the text in quotes, “essential”. I inputted the cipher into decode as a Vigenere Decode with the key “essential” and got a result, as seen in Figure 2.4.
- flag
- MapleTrees
BASH these ROTten criminals (10 points)
rj vuzcj n mncczza
I was not able to complete this challenge yet.
Why did the stego expert wear a ‘cloak’? To keep their messages undercover! (10 points)
We hope you are having a great day!
I was not able to complete this challenge yet.
What is your favorite SHAKESPEARE play? (10 points)
lv bo sj cst ks tl, trel xw tyi ibecxadr
I was not able to complete this challenge yet.
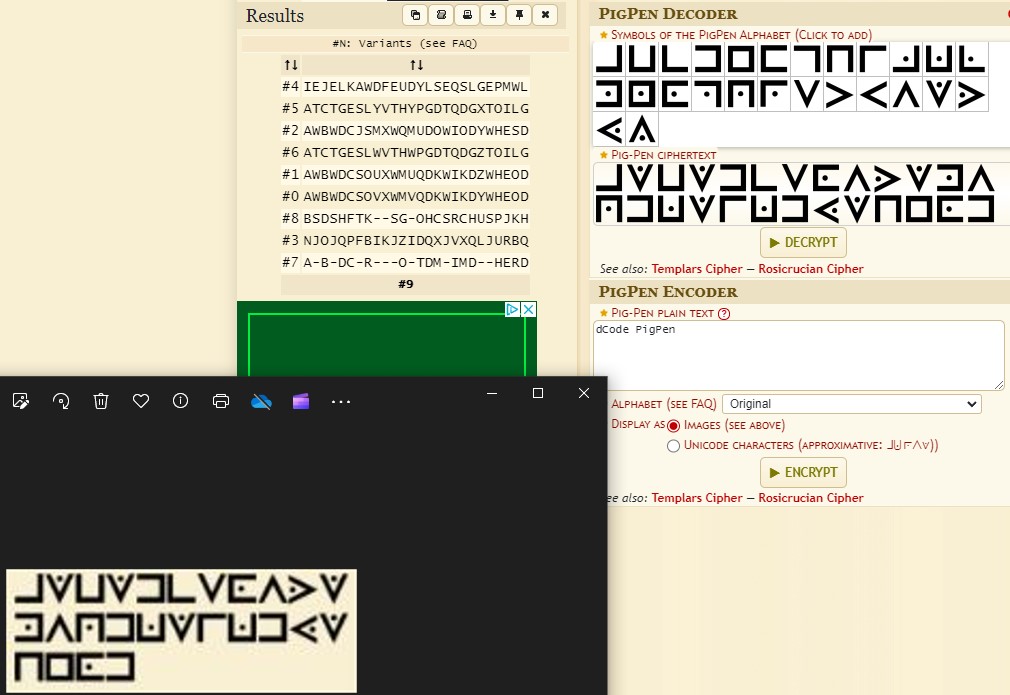
Giovan Battista Bellaso probably LOVED pigs (10 points)
Giovan.JPG
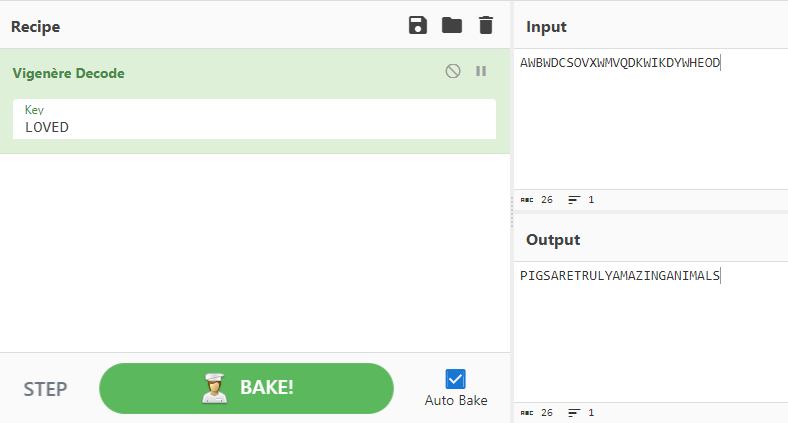
The attached picture, along with “pigs” being in the challenge name, hinted at this being a pigpen cipher. As seen in Figure 2.8.1, I used decode.fr to get an output for the pigpen cipher.
After reading into the pigpen cipher details, number 0 would be the correct output for the type of pigpen inputted. This output was “AWBWDCSOVXWMVQDKWIKDYWHEOD”. Thought that this would be a Bellaso cipher after, but no dice. Since we had a key indicated by the capitalized LOVED, I tried a Vigenere decode in CyberChef with the key LOVED, and got an output, as seen in Figure 2.8.2.
- flag
- PIGSARETRULYAMAZINGANIMALS
Surfing sound waves in California searching for hidden messages (25 points)
Song.wav
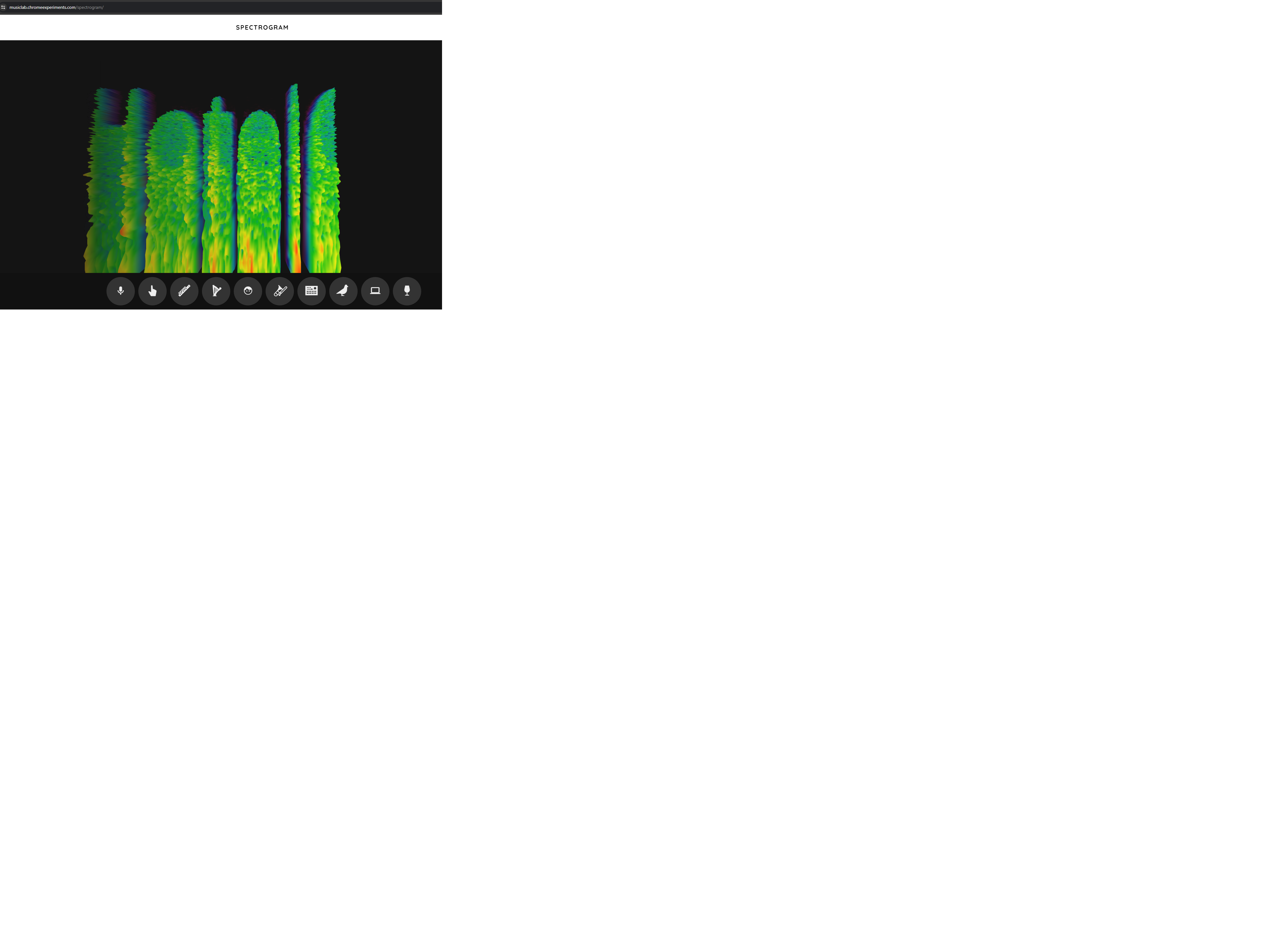
I knew after listening to this file that some sort of sound tool was needed. I first loaded the file into Audacity. I could not find anything significant, so I looked into more clues, researching how to hide messages in audio files. I thought the Audacity files looked significant in some way, and guessed it might be visual based. I found the tool “https://musiclab.chromeexperiments.com/spectrogram/” and loaded the audio file into it. Across the screen, a message appeared, as seen in Figure 2.9.
- flag
- Hotel California
ROTten people hiding their secrets! (25 points)
Steganography.rtf
I was not able to complete this challenge yet.
EXIF data, the memory foam of photography, never forgets the shot you took! (50 points*)
nicedog.jpg
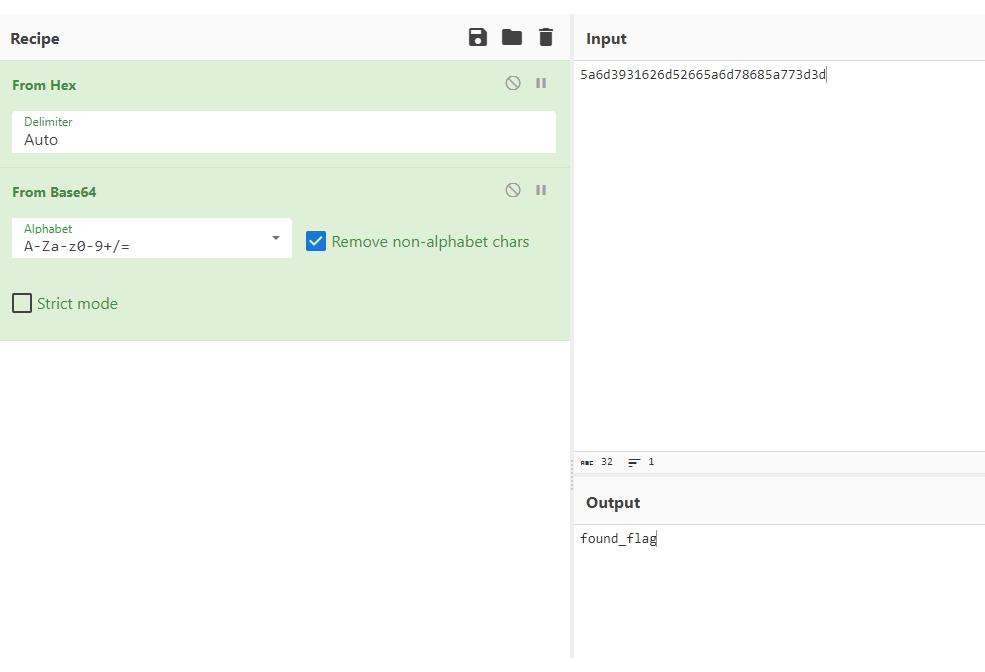
Given the EXIF hint, I used ExifTool and loaded “nicedog.jpg” into the tool. The Lens serial number seemed a bit off, as seen in Figure 2.11.1, so I copied it out and loaded it into CyberChef. 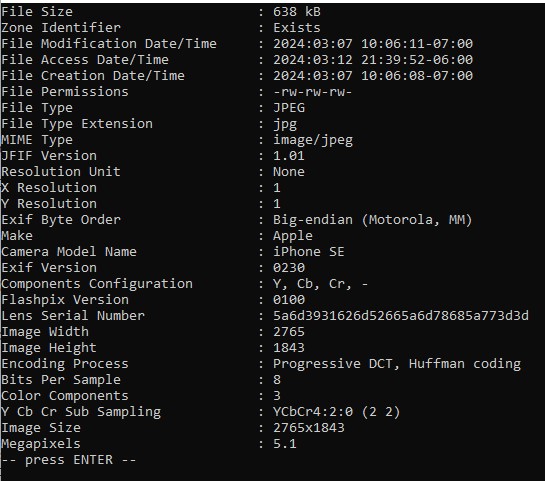 Figure 2.11.1
Figure 2.11.1
“5a6d3931626d52665a6d78685a773d3d” seemed at best bet, hex. I decoded from Hex, and noticed a “=” at the end of the text, so I decoded again from Base64. The resulting flag was “found_flag”, as seen in Figure 2.11.2.
- flag
- found_flag
Android
All flags were found using the “Google Pixel 3a XL Logical Image - Data.tar” image, “Discord.zip”, and “facebook-61554919820462-2024-01-06-49fzodcA.zip” for this section.
The following flags were not found (yet) for Android and will be updated when they are:
- A game of Cat and Mouse
- Always achieving new heights
- LIVE your life
- Out of Stock
Press x to Respawn (5 points*)
On what platform did Rocco share his Call of Duty Username?
As we know from iOS challenges, a common acronym for Call of Duty is CoD. In AXIOM, using the keyword “cod”, there are results under the section “SOCIAL NETWORKING” under “Twitter Direct Messages”. Here, you can see that Rocco shares his CoD username with Chad over Twitter DMs, as seen in Figure 3.1.
- flag
Warm Up (5 points*)
What Southern state’s sports team did Rocco search up? (STATE ONLY)
For this challenge, I looked under AXIOM’s “REFINED RESULTS” section, under “Google Searches”. A few down, a search for “ragin cajuns football record” is found (Figure 3.2). . A qui
A quick google search shows that the team Ragin Cajuns are from Louisiana.
- flag
- Louisiana
Can you Handle this (5 points*)
What was Rocco’s Twitter account name?
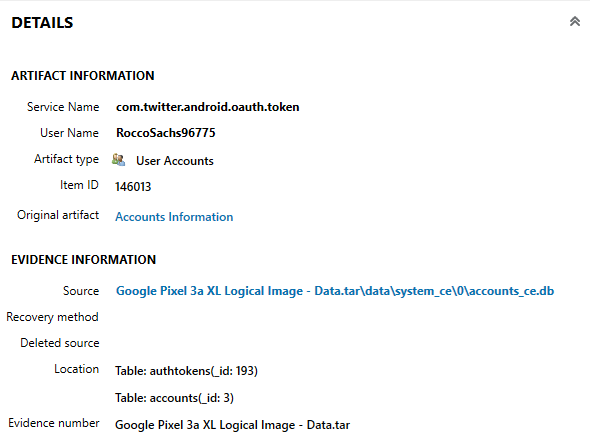
Under AXIOM’S “REFINED RESULTS” section, under “User Accounts”, the account name for Twitter can be seen, as seen in Figure 3.3.
- flag
- RoccoSachs96775
Need to reach those heights (5 points)
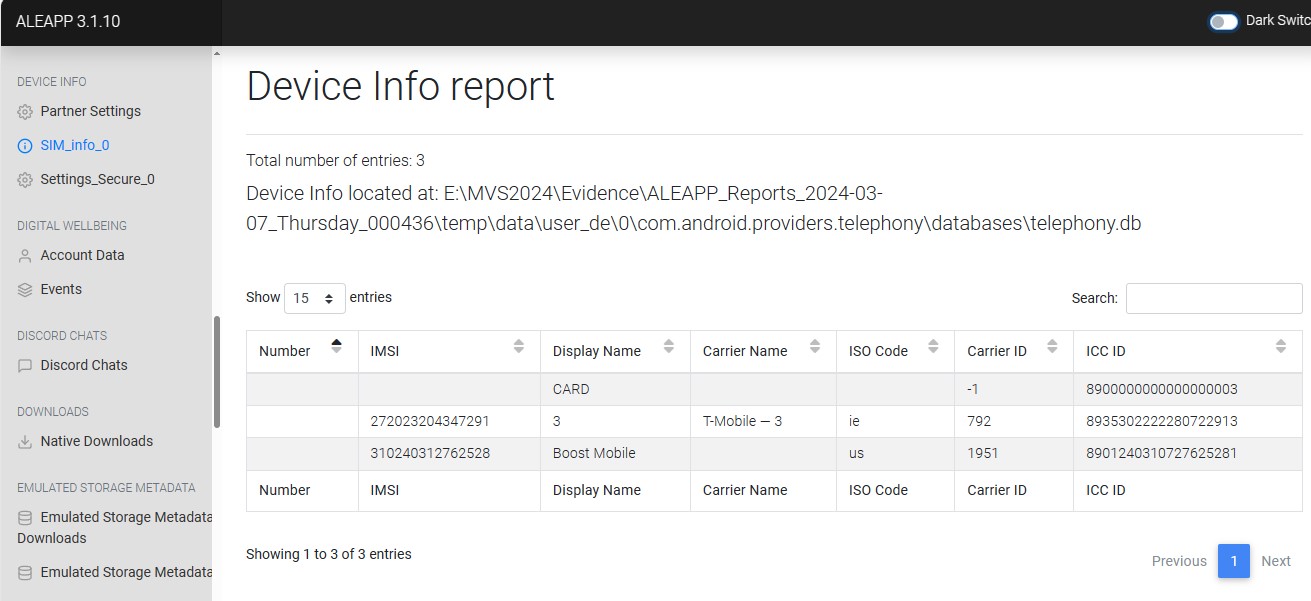
What is the SIM operator name?
In the report generated by aLEAPP, there is a section named “Device Info”, with a subsection of “SIM_info_0”. As seen in Figure 3.4, the SIM card is associated with Boost Mobile.
“T-Mobile -3” is also listed, but due to the hint in the challenge, I Figured Boost would be correct, and it was. The artifact location associated with this answer is “\data\user_de\0\com.android.providers.telephony\databases\telephony.db”.
- flag
- Boost
Not to be basic but… (5 points*)
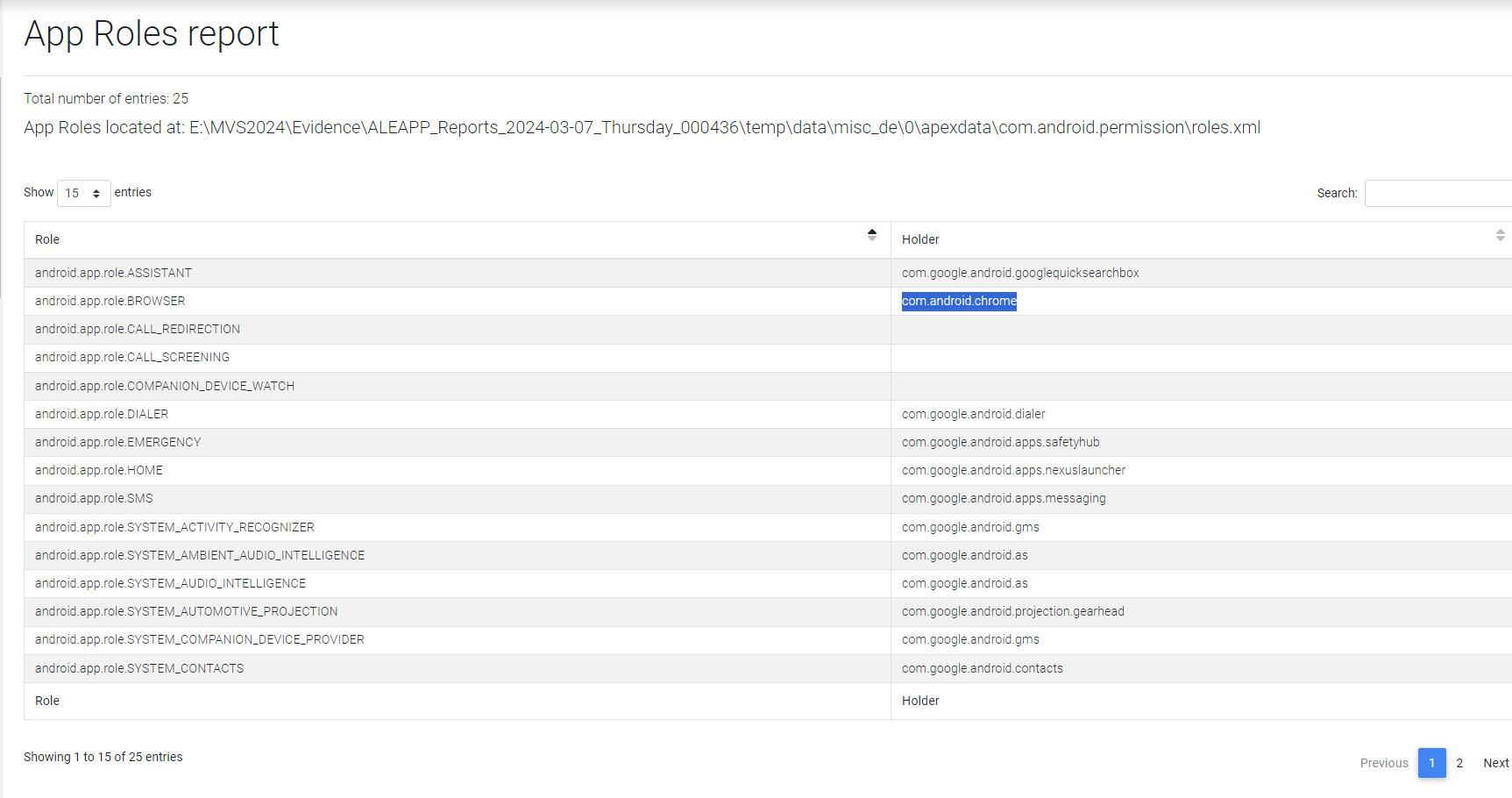
What is the default Internet Browser?
In aLEAPP, under the “APP ROLES” section, “Android 11 Roles_0” subsection, the role “android.app.role.BROWSER” is set to com.android.chrome. The artifact for this can be found at “\data\misc_de\0\apexdata\com.android.permission\roles.xml”. As seen in Figure 3.5, the default browser is Chrome.
- flag
- Chrome
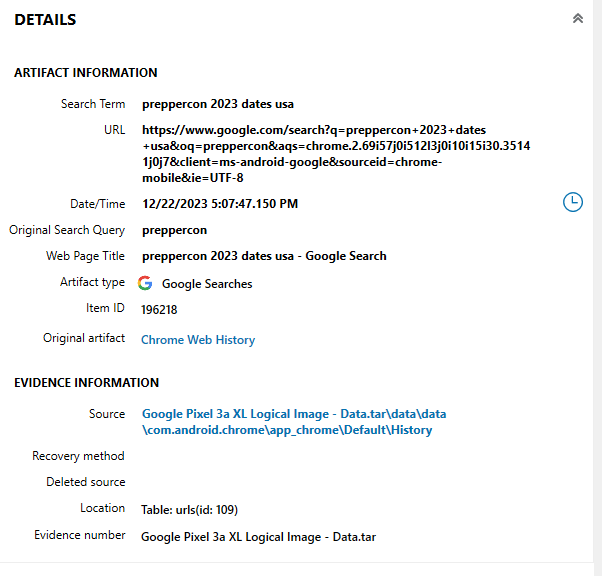
Survival Mode Activated (5 points*)
What conference did Rocco show interest in?
For this challenge, I looked under AXIOM’s “REFINED RESULTS” section, under “Google Searches”. Not too far down, as seen in Figure 3.6, there is searched for “preppercon”.
- flag
- Preppercon
Sign me up! (5 points*)
What email is associated with the device?
Under AXIOM’S “REFINED RESULTS” section, under “User Accounts”, the account name for com.google can be seen, as seen in Figure 3.7. 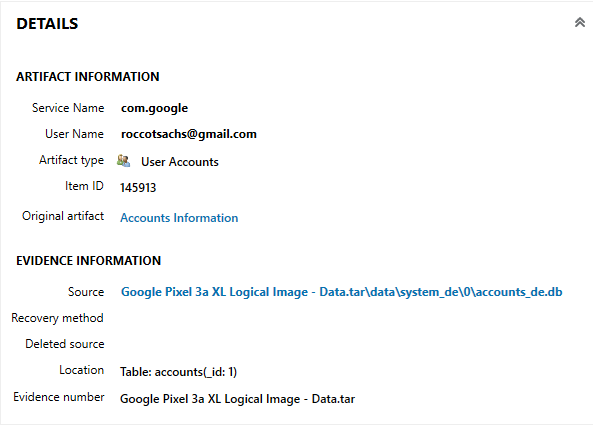 Figure 3.7
Figure 3.7
- flag
- roccotsachs@gmail.com
Not so popular (5 points)
How many messages were sent from Rocco in Twitter Direct Messages?
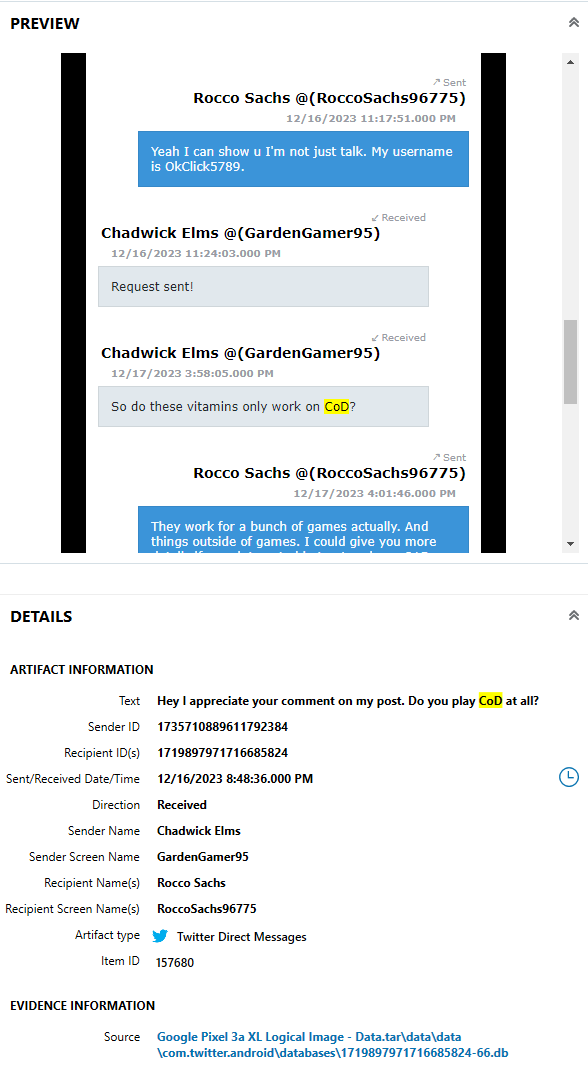
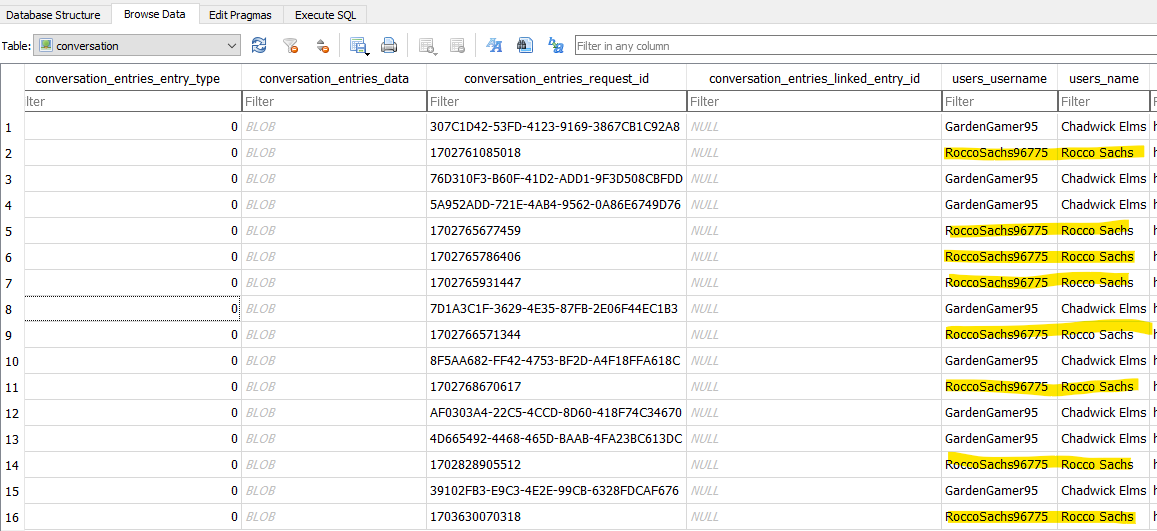
By going to the “SOCIAL NETWORKING” section and “Twitter Direct Messages” subsection in AXIOM, many Twitter DMs can be seen. It is a bit noisy with the results, so the source file, found at “data\data\com.twitter.android\databases\1719897971716685824-66.db”, was opened in DB Browser. Under the conversation table, it can quickly be seen which messages were from who. As seen in Figure 3.8, Rocco receives messages and sends messages 8 times.
- flag
- 8
You can never be too ready (10 points)
How many additional survival tips were provided in the $9 book Rocco was looking into?
In AXIOM, I did a keyword search for “survival”. In Chrome web history, there was a result for the link “https://www.amazon.co.uk/How-Fight-Bear-Win-Survival/dp/1645171345?ref=d6k_applink_bb_dls&dplnkId=dd217c0b-bb6e-43b3-924a-e0833944d9b6”. I opened the link in Incognito, where I could see the full book is named “How to Fight a Bear…and Win: And 72 Other Real Survival Tips We Hope You’ll Never Need” as seen in Figure 3.9, priced around $9. 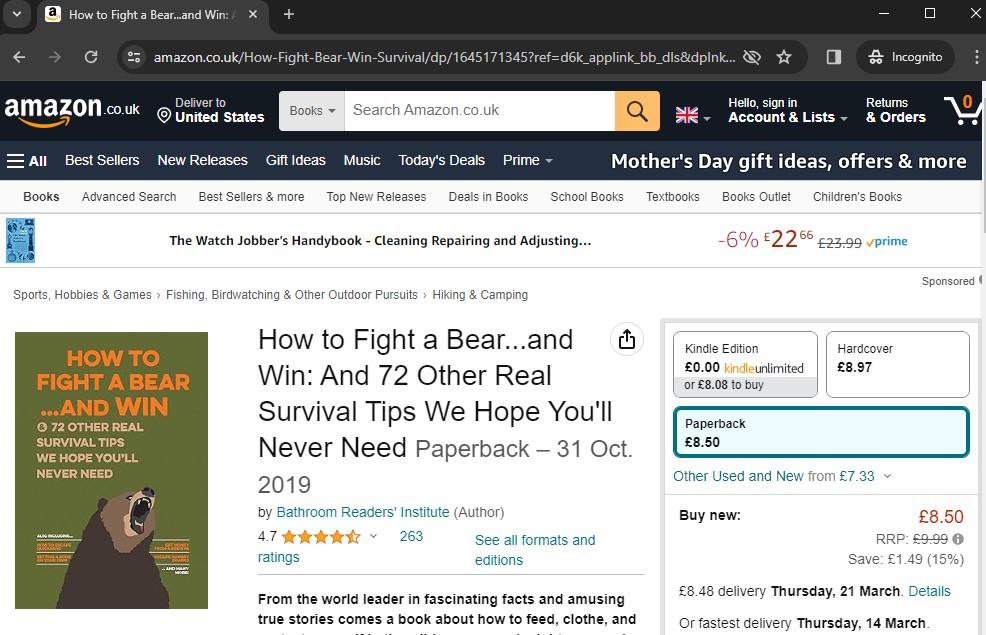 Figure 3.9
Figure 3.9
Also, a picture of the book can be “data\media\0\DCIM\Camera\PXL_20231215_202654750.jpg”, where it is actually priced $9.
- flag
- 72
Tag you’re it! (10 points)
What city was the user in when they identified an AirTag on them?
In the aLEAPP report, latitude and longitude for “Android Airtag Scans” can be found under the “AIRTAG DETECTION” section, as seen in Figure 3.10.1. 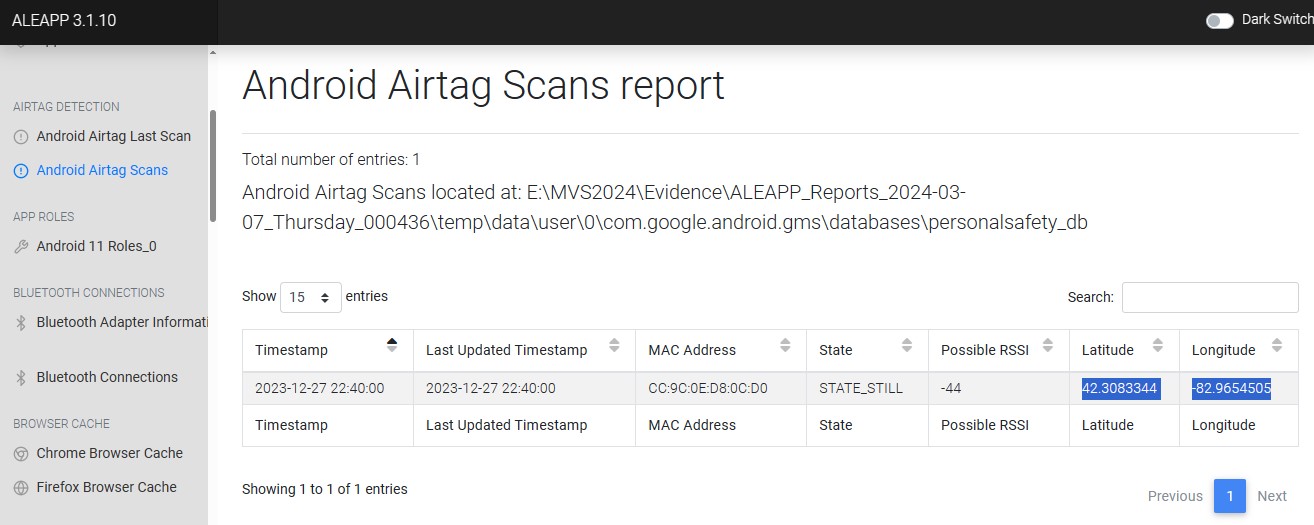 Figure 3.10.1
Figure 3.10.1
These coordinates were entered in google maps, showing a location in Windsor, as seen in Figure 3.10.2. 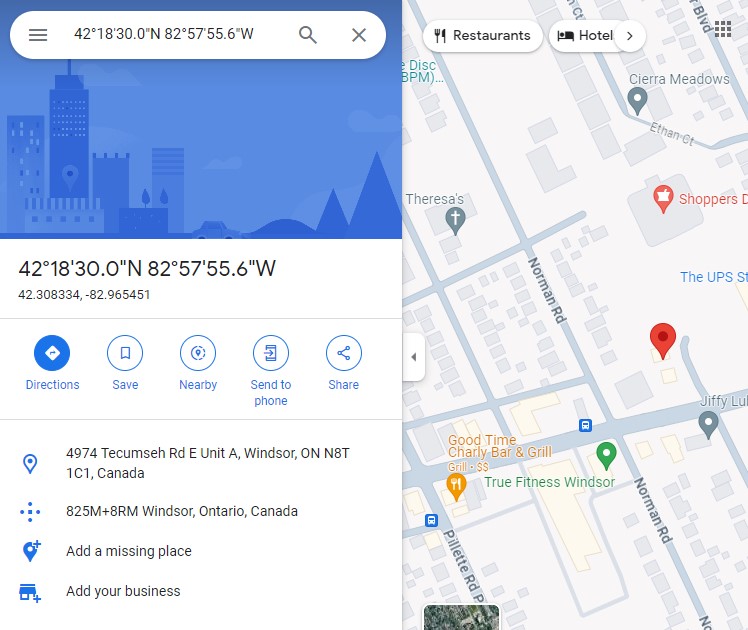 Figure 3.10.2
Figure 3.10.2
- flag
- Windsor
A game of Cat and Mouse (10 points)
What game did two beloved characters promote in an Ad?
I was not able to complete this challenge yet.
Always achieving new heights (10 points)
What was the new score achieved on the video game Rocco watched on YouTube?
I was not able to complete this challenge yet.
Remember your floaties (10 points)
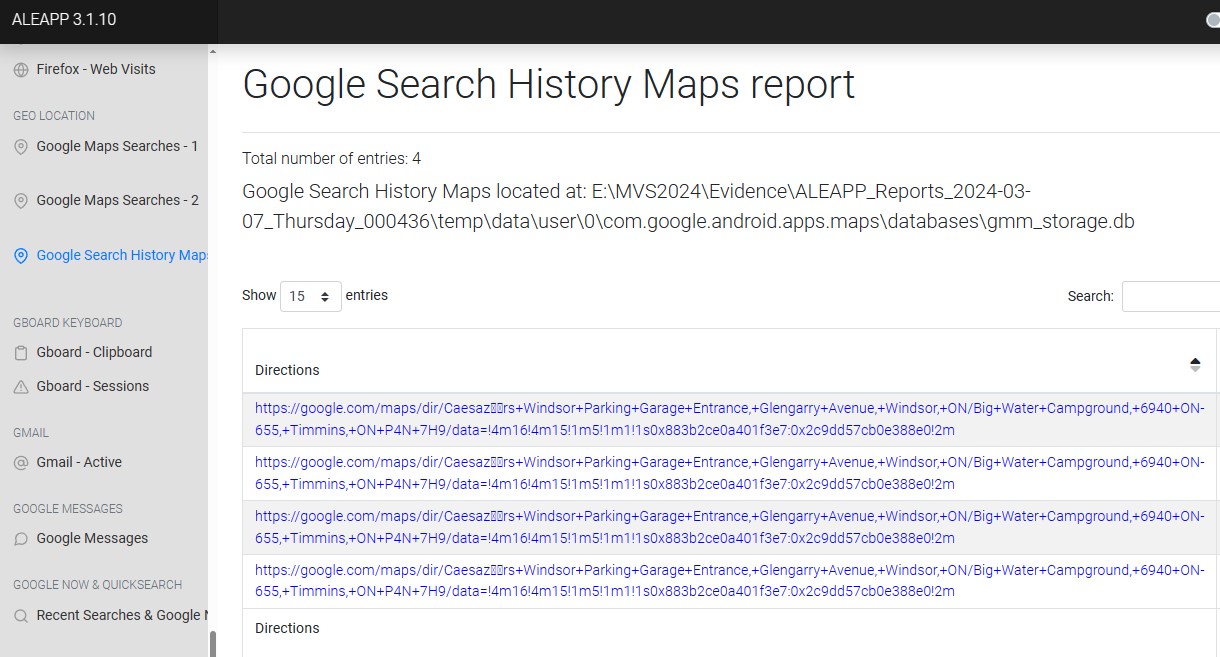
What fun outdoor activity location was searched for?
I could sworn I entered this flag during the CTF, but must have fat-fingered it. Anyways, in aLEAPP, there a nifty “GEO LOCATION” section, with a subsection for “Google Search History Maps”. As seen in Figure 3.13, there is a search for “Big Water Campground”.
- flag
- Big Water Campground
R-E-J-E-C-T-E-D Rejected (10 points)
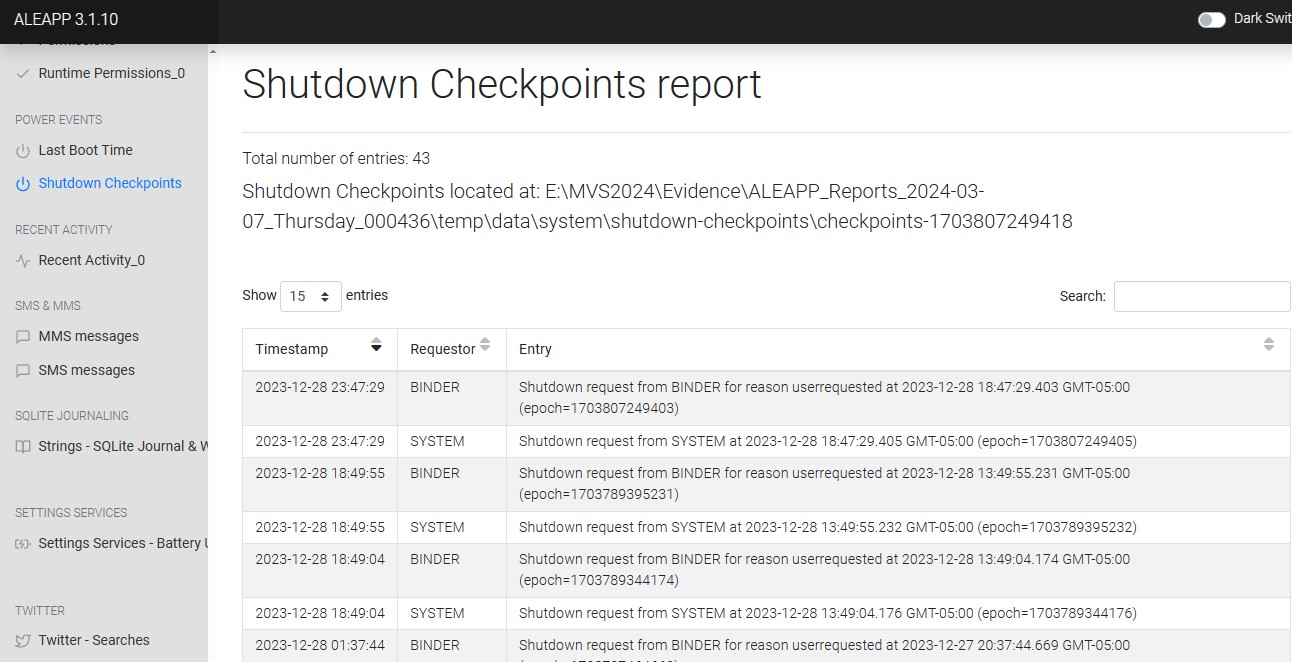
When was the last shutdown that was initiated by Rocco? (YYYY-MM-DD HH:MM:SS) UTC 24 hour time.
In aLEAPP under the “POWER EVENTS” section, there is a report for “Shutdown Checkpoints”. I sorted by most recent, and first entry that did not have a requestor of “system” was “2023-12-28 23:47:29 UTC”, as seen in Figure 3.14.
Artifact location is “data\system\shutdown-checkpoints\checkpoints-1703807249418”.
- flag
- 2023-12-28 23:47:29
No two cents about them (10 points x 2*)
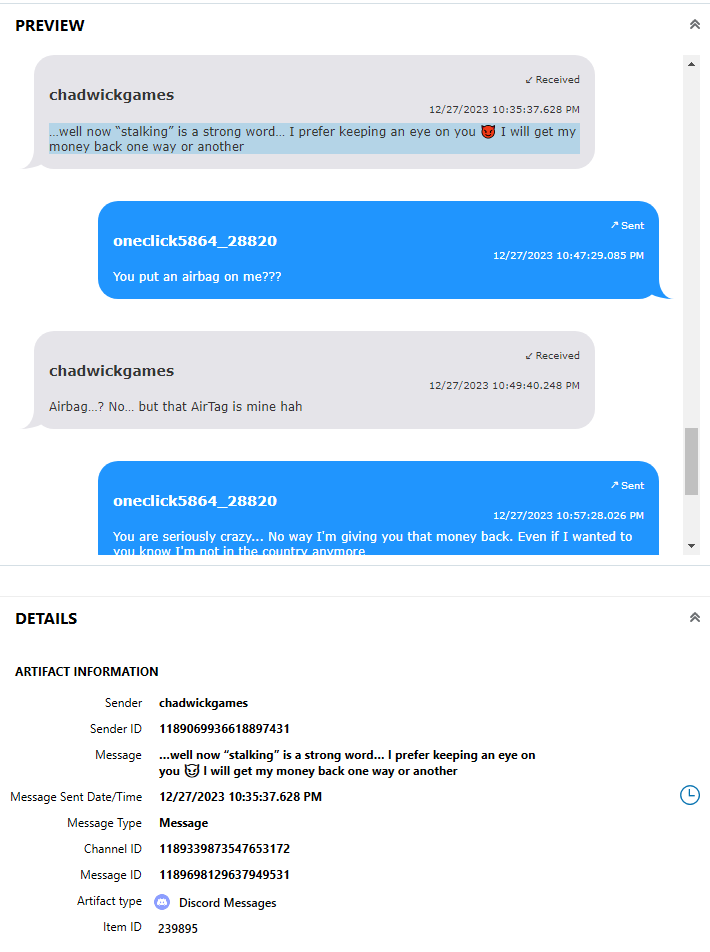
According to exCHANGEs in discord with Chad, what did Chad want back from Rocco?
In AXIOM, under the “COMMUNICATION” section and “Discord Messages” subsection, there is a few messages between Rocco and Chad. A specific message, seen in Figure 3.15, shows Chad mentioning wanting his money back.
This challenge was listed twice, so 10 free points!
- flag
- money
Out of Stock (25 points)
What is the most recent score in Subway Surfer
I was not able to complete this challenge yet.
So Salty!(25 points*)
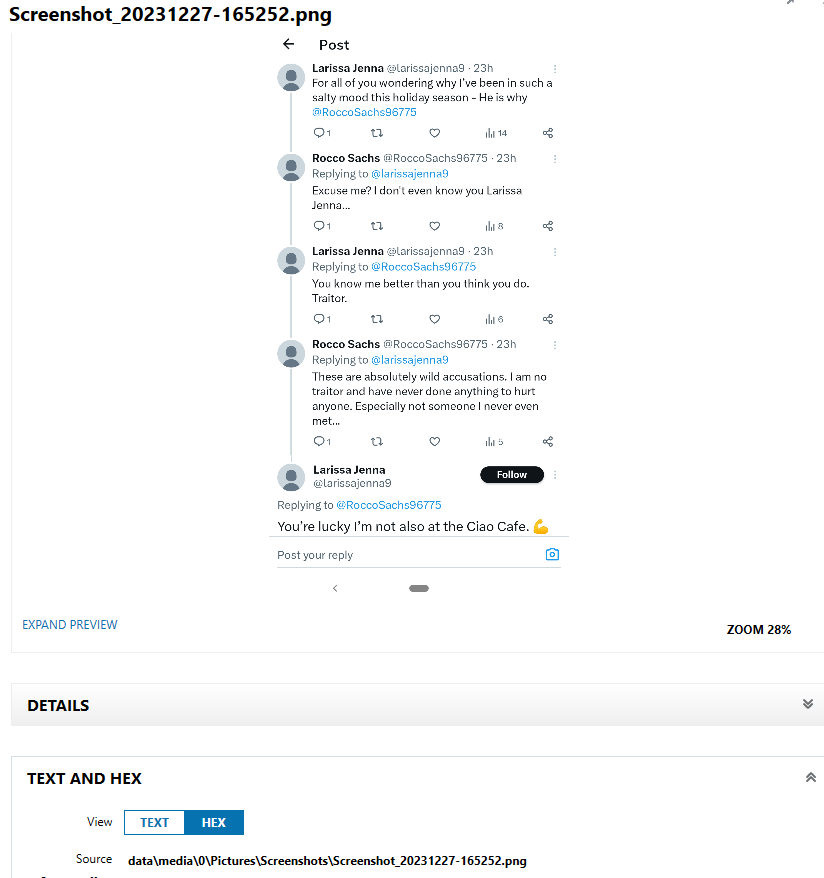
What is the handle of the person who is talking about how upset they are with Rocco?
In the photo “data\media\0\Pictures\Screenshots\Screenshot_20231227-165252.png”, Larissa Jenna is tweeting angrily back and forth with Rocco. As seen in Figure 3.17, their twitter handle is @larissajenna9.
- flag
- @larissajenna9
Secrets Secrets are no Fun (25 points*)
What did Rocco search in the App Store to download the app used to hide photos?
In AXIOM, I looked at the “APPLICATION USAGE” section and “Google Play Searches” subsection. The search term including “vault” stuck out to me, with the full term being “calculator vault”, as seen in Figure 3.18.
A quick google search confirms that this app hides photos.
- flag
- calculator vault
LIVE your life (25 points)
What two sports did rocco capture in a photo (__ and __)
I was not able to complete this challenge yet.
Don’t let them see you down (25 points*)
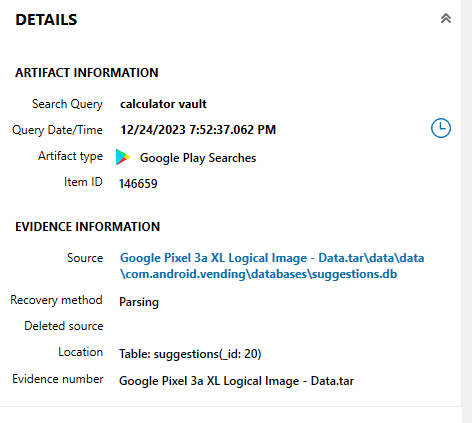
What was added using photoshop
While browsing photos before, I had noticed a folder with Photoshop in the name at “data\media\0\Pictures\Photoshop Express". The image “PSX_20231226_160226.png” shows a NYTimes Connections game with a heart with “success” in it added, as shown in Figure 3.20.
flag :success
It’s the eye of the tiger (25 points*)
When is Rocco’s Bday? (YYYY-MM-DD)
This flag can be found in the Facebook dataset under “personal_information\profile_information\profile_information.html”. The HTML file contains basic profile information, included Rocco Sachs’ birthday, as seen in Figure 3.21. 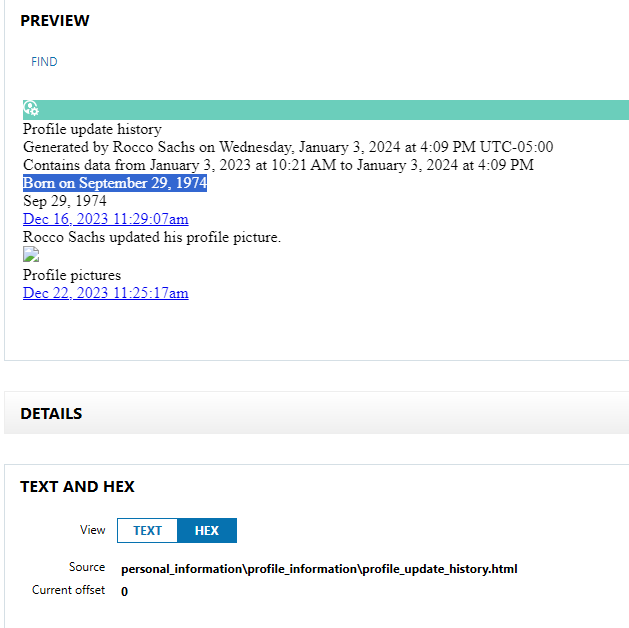 Figure 3.21
Figure 3.21
- flag
- 1974-09-29
Stalker Alert (50 points)
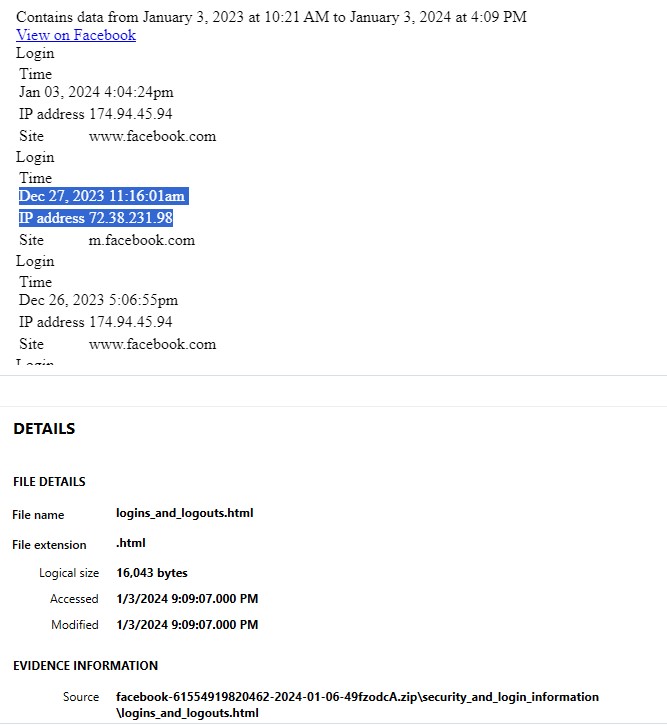
Shortly after logging into Facebook with IP address 72.38.231.98, a photo was taken. Where was this photo taken?
In the provided Facebook logs there is only one entry that has an IP address of 72.38.231.98. That login had a timestamp of 12/27/2023 11:16:01 UTC, as seen in Figure 3.22.1.
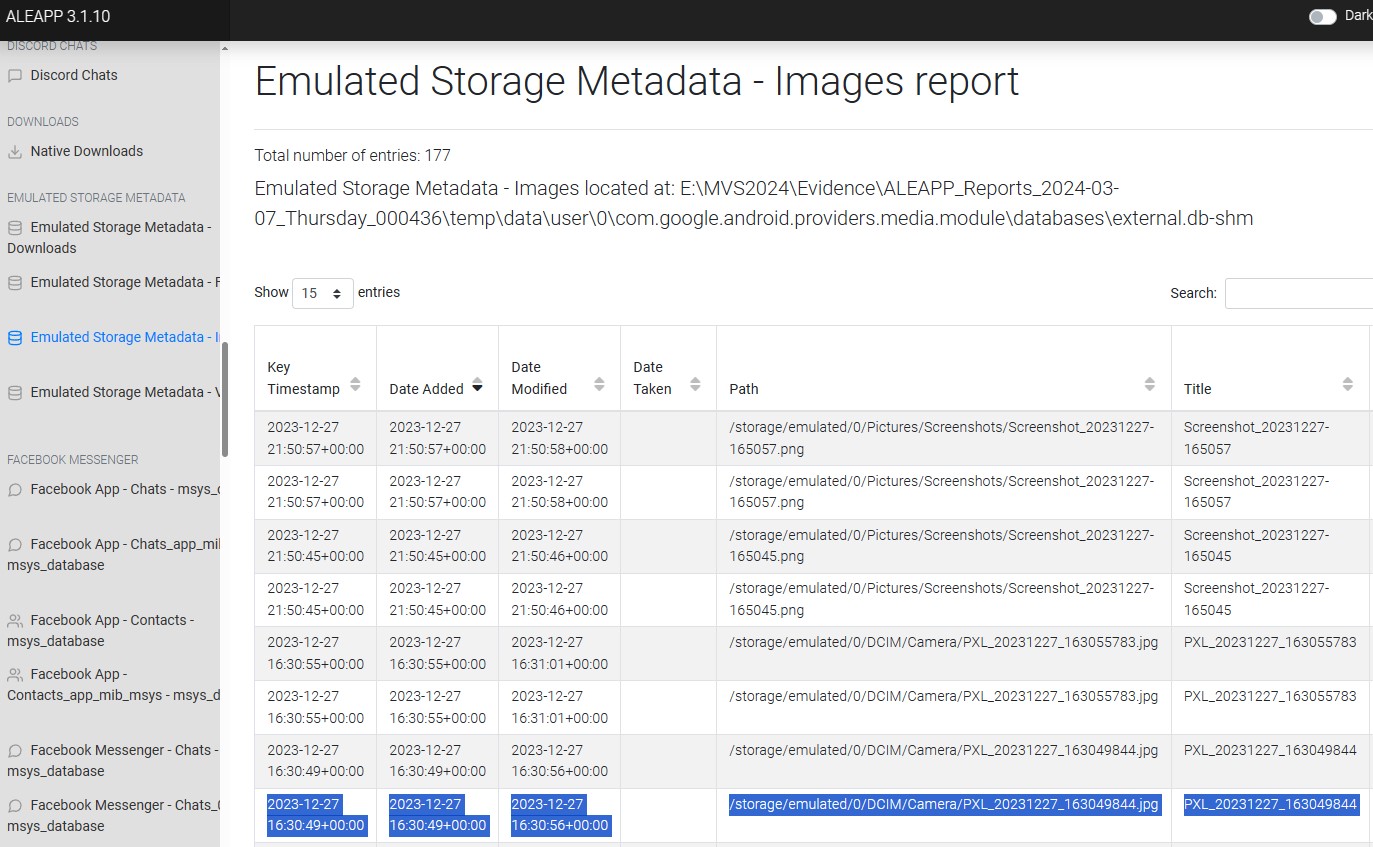
In aLEAPP, I looked at photos and their timestamps. There was one photo taken a few hours after the Facebook login, the most recent one since the login, “/storage/emulated/0/DCIM/Camera/PXL_20231227_163049844.jpg”, as seen in Figure 3.22.2.
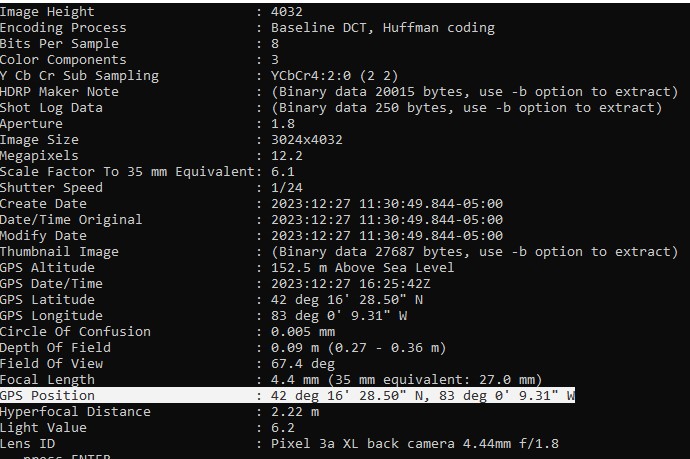
I exported the photo from Axiom and loaded it into EXIF Tool v12.62, where I copied out the field “GPS Position”, as seen in Figure 3.22.3.
The GPS Position coordinates, 42°16’28.5”N 83°00’09.3”W , were entered into Google Maps. It can be seen from there (Figure 3.22.4) that the photo was taken at Devonshire Mall.
- flag
- Devonshire Mall